Blast-RADIUS Vulnerability: How to protect your organization
July 10, 2024 •
What is the Blast-RADIUS Vulnerability?
The Blast-RADIUS vulnerability was published by researchers on July 9, 2024, and it affects the RADIUS protocol, which is commonly used for authentication, authorization, and accounting (AAA) in enterprise and telecommunication networks.
By exploiting flaws in the RADIUS protocol, a Man-in-the-Middle (MITM) attacker can trivially forge RADIUS requests and responses between a RADIUS client and a RADIUS server, and can “forge a valid protocol accept message in response to a failed authentication request”. This enables the attacker to gain access to network devices and services protected by the RADIUS authentication. The attacker doesn’t need to learn user credentials, either through guesswork, brute force attacks, or account compromise.
Are LoginTC services impacted?
The Blast-RADIUS vulnerability affects all RADIUS implementations that use non-EAP authentication methods over plain UDP or TCP. This includes the LoginTC RADIUS Connector.
How can I protect against Blast-RADIUS?
The latest version of the LoginTC RADIUS Connector (4.0.11) includes several new features that protect your organization against Blast-RADIUS attacks. There are several short-term mitigations in addition to a long-term mitigation.
LoginTC RADIUS Connector 4.X
Upgrade in place to 4.0.11: upgrade guide
LoginTC RADIUS Connector 3.X or lower
The LoginTC RADIUS Connector 3.X virtual appliance is end of life. Upgrade to the latest version: step-by-step upgrade guide
Recommendation 1: Require RADIUS Clients to send Message-Authenticator attributes
Require clients to include a Message-Authenticator RADIUS attribute on each request. This attribute is a message authentication code over the entire packet and is not believed to be affected by the vulnerability.
Administrator action: Upgrade all network devices and services that act as RADIUS clients and enable them to send Message-Authenticator attributes. Many RADIUS clients do not send a Message-Authenticator attribute in RADIUS requests unless configured. Many RADIUS clients also do not support Message-Authenticator attributes. Refer to your vendor documentation for instructions on how to upgrade or to enable Message-Authenticator attributes.
Administrator action: LoginTC RADIUS Connector version 4.0.11 adds a configurable option to require Message-Authenticator attributes from RADIUS clients. All new Endpoints will have this flag set to enabled by default. Existing and imported endpoints should be updated as the RADIUS clients are upgraded:
- Log into the LoginTC RADIUS Connector web based interface
- Go to Endpoints
- Click your endpoint
- Scroll down to Client Settings, click Edit
- Scroll down to Require Message-Authenticator, select Yes, require the Message-Authenticator attribute
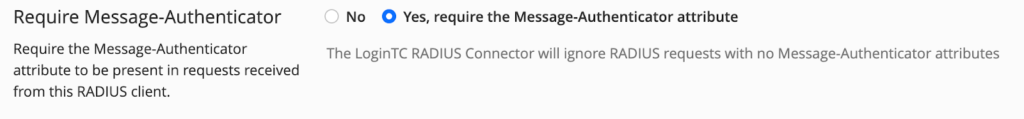
- Scroll down, Click Test and Update
Recommendation 2: Limit Proxy-State attributes
In the case where a RADIUS client is not yet updated or can not be updated (e.g., due to end-of-life hardware), limiting the use of certain RADIUS attributes makes the vulnerability more difficult to exploit. Requiring the Message-Authenticator attribute to be present in requests received from a RADIUS client when there is a Proxy-State attribute present makes the vulnerability more difficult to exploit.
Administrator action: Upgrade all network devices and services that act as RADIUS clients and enable them to send Message-Authenticator attributes alongside Proxy-State attribute if used. Refer to your vendor documentation for instructions on how to upgrade or to enable Message-Authenticator attributes if and when the Proxy-State is used.
Administrator action: LoginTC RADIUS Connector 4.0.11 adds a flag to limit Proxy-State attributes. All new Endpoints will have this flag set to enabled by default. Existing and imported endpoints should be updated as the RADIUS clients are upgraded:
- Log into the LoginTC RADIUS Connector web based interface
- Go to Endpoints
- Click your endpoint
- Scroll down to Client Settings, click Edit
- Scroll down to Limit Proxy-State, select Yes, limit Proxy-State attributes
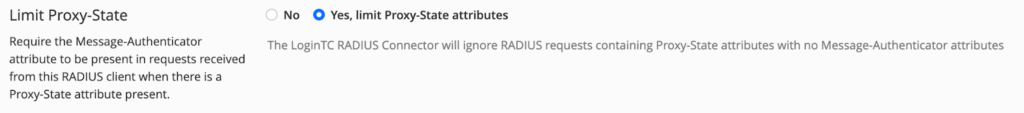
- Scroll down, Click Test and Update
Recommendation 3: Always send Message-Authenticator attribute
The RADIUS server should always include a Message-Authenticator attribute in RADIUS responses.
Administrator action: None. LoginTC RADIUS Connector 4.0.11 ensures that a Message-Authenticator attribute is always set when sending back RADIUS responses to RADIUS clients. LoginTC RADIUS Connector 4.0.11 also includes a Message-Authenticator attribute when it acts as a RADIUS client.
Long-term Recommendation: RADIUS over TLS
The long-term recommended mitigation is to use RADIUS inside modern cryptographically-protected transport layers such as TLS. The IETF RADIUS EXTensions working group has existing experimental and draft RFCs for RADIUS over TLS, including one common implementation known as RadSec.
Future releases of the LoginTC RADIUS Connector will implement future protocol changes and also include support for RADIUS over TLS, including RadSec.
Administrator action: Install patches and upgrades to the LoginTC RADIUS Connector as soon as they are available.
Administrator action: Install patches and upgrades to network devices as soon as they are available.
Get support
If you have additional questions or need help, contact LoginTC support by emailing us at support@cyphercor.com.