How to protect your organization against Citrix Bleed
December 20, 2023 •
Introduction
The latest vulnerability affecting Citrix systems, known as Citrix Bleed, has emerged as a critical threat to the private data of organizations and individuals around the world. This critical security issue has impacted countless companies and individuals globally, emphasizing the need for better security measures.
In this blog post, we will explore what the Citrix Bleed vulnerability is, how to protect against it, and what additional steps you can take to help make your organization more secure.
What is Citrix Bleed?
Citrix Bleed is a vulnerability officially known by the designation CVE-2023-4966 that affects Citrix NetScaler ADC and NetScaler Gateway. Citrix Bleed allows legitimate user sessions to be ‘hijacked’ by malicious actors by leveraging a vulnerability in the buffer overflow configuration of these services, similar to the Heartbleed exploit from several years ago. By exploiting this vulnerability, sensitive information and authenticated session tokens can be stolen.
This vulnerability has already affected a number of major organizations, including Boeing, the Industrial and Commercial Bank of China, and scores of other organizations both large and small. The ripple effects of this vulnerability are likely to be felt for months to come, as companies continue to investigate for malicious activity and work to fix the issue.
How do you fix the Citrix Bleed vulnerability?
The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing & Analysis Center (MS-ISAC), and Australian Signals Directorate’s Australian Cyber Security Center (ASD’s ACSC) released a joint advisory along with a report analyzing the vulnerability.
These organizations have instructed anyone operating the following appliances to update them, scan for malicious activity, and report anything suspicious to CISA:
- NetScaler ADC and NetScaler Gateway 14.1-8.50 and later releases
- NetScaler ADC and NetScaler Gateway 13.1-49.15 and later releases of 13.1
- NetScaler ADC and NetScaler Gateway 13.0-92.19 and later releases of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.164 and later releases of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.300 and later releases of 12.1-FIPS
- NetScaler ADC 12.1-NDcPP 12.1-55.300 and later releases of 12.1-NDcPP
Additionally, Citrix has said that even after updating, compromise may still be possible through existing active sessions. In order to fully protect your organization, it’s recommended to shut down any existing active sessions.
How to boost your Citrix security after patching
Even after updating your software and removing any suspicious activity, you may still want to take this as an opportunity to improve your security overall.
Here are some recommended next steps:
- Limit attack surface: Eliminate redundancies, introduce policies, and apply principles of least privilege to ensure that you’re only using the services you need, and users only have access to what’s required for their role.
- Enable encryption: Secure communication flows with TLS, implement public key encryption into NetScaler, utilize LDAP protocols where applicable, and opt for the highest level of encryption whenever possible.
- Introduce comprehensive MFA: Don’t just rely on in-house multi-factor capabilities. Consider adding a comprehensive MFA solution to your Citrix applications, such as LoginTC’s Citrix NetScaler connector.
Benefits of the LoginTC Citrix NetScaler connector
The LoginTC Citrix connector integrates seamlessly with Citrix NetScaler to provide enhanced MFA operations and monitoring. While Citrix offers the ability to turn on MFA, here are some reasons to consider a dedicated MFA solution:
1. Wide variety of authentication methods
With the LoginTC Citrix connector, you have access to a significantly wider range of authentication methods than what Citrix offers internally. From push notification authentication, to software and hardware OTP, to FIDO2 tokens, to passcode grids, and more, you can choose the authentication methods that work best for your organization and your users.
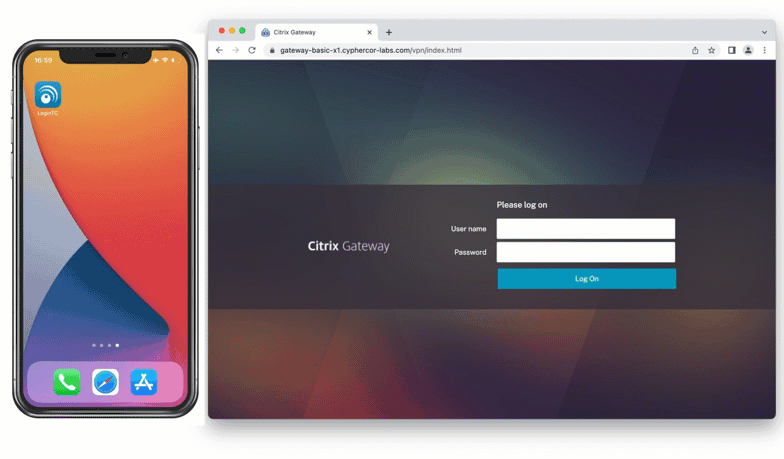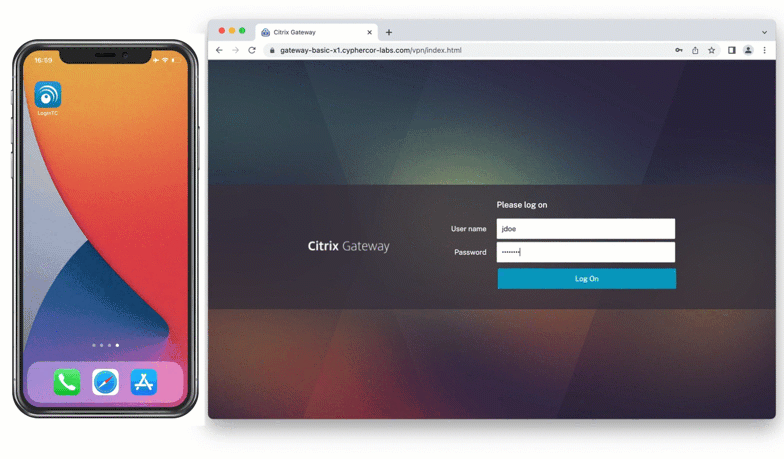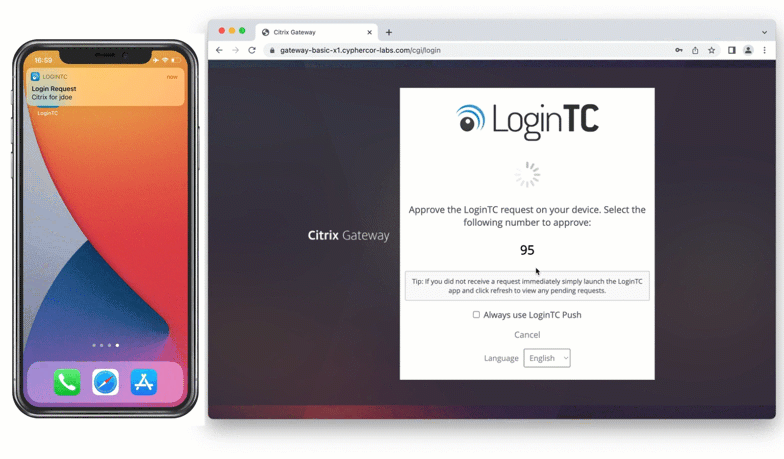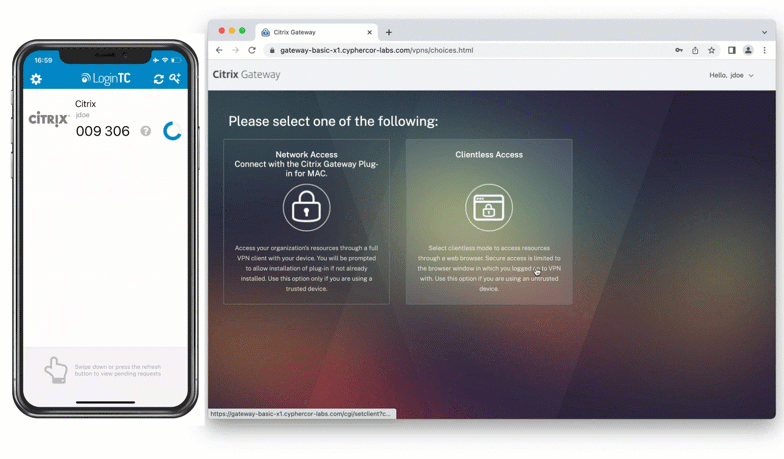
Push Number Matching with Citrix Gateway

Hardware Token Authentication with Citrix Gateway
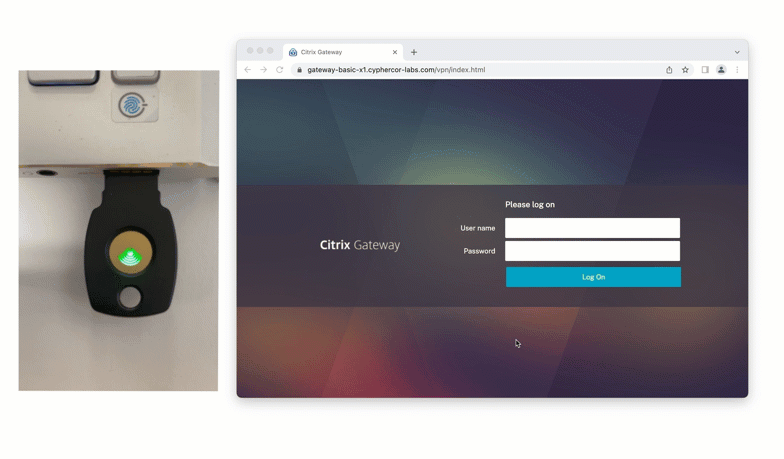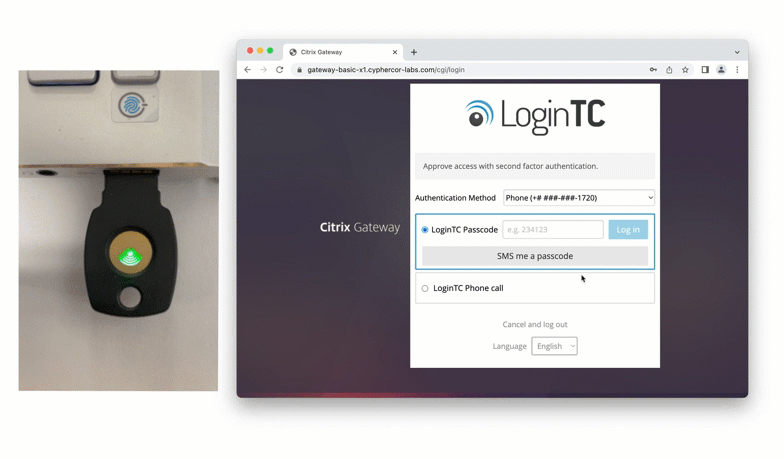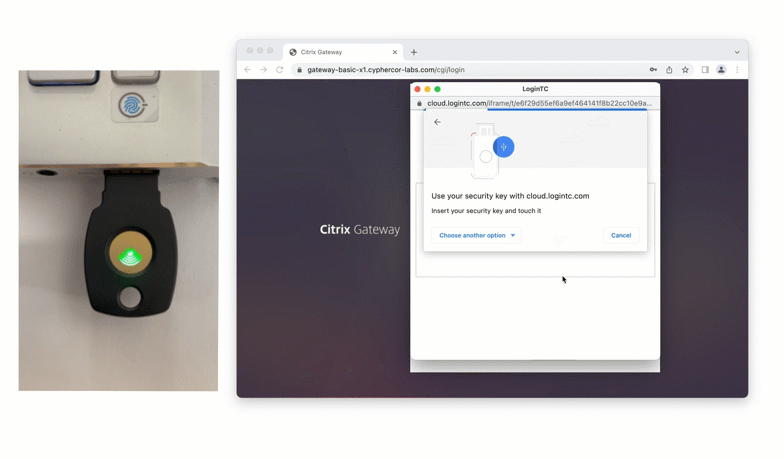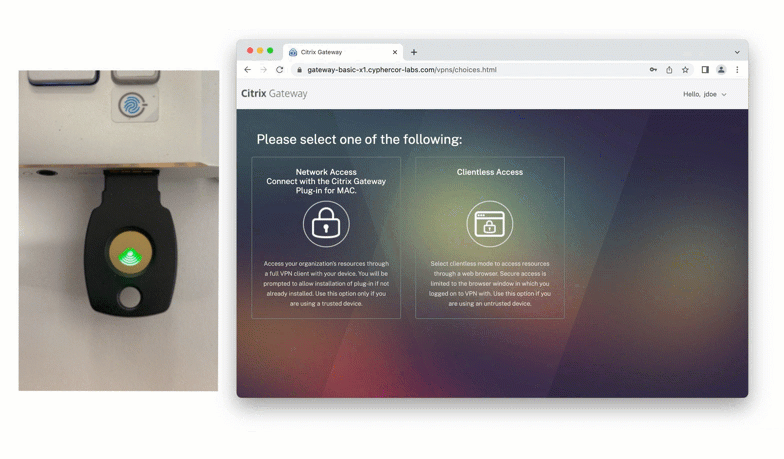
FIDO2 Authentication with Citrix Gateway
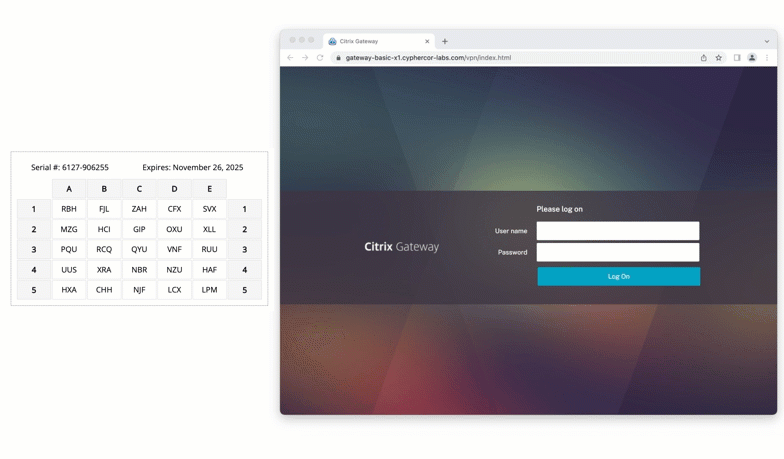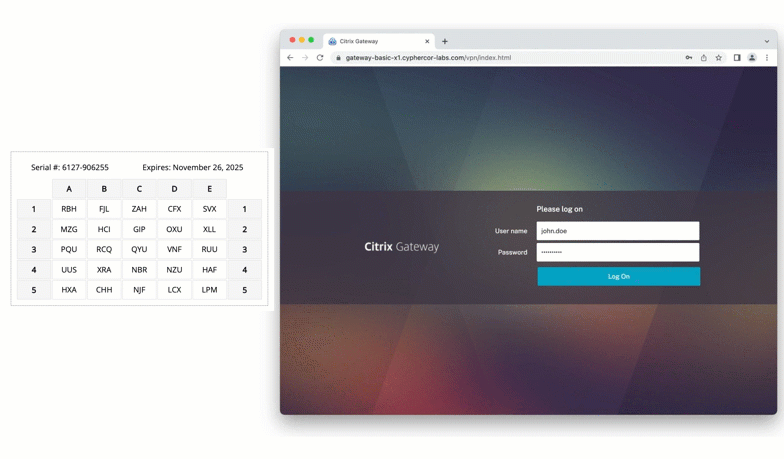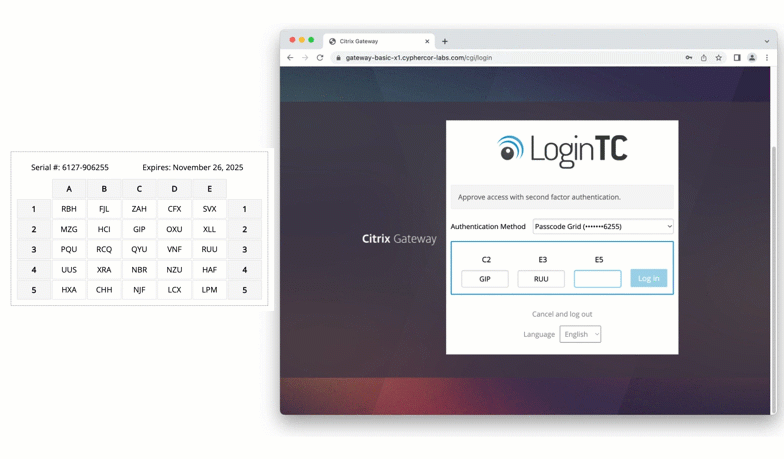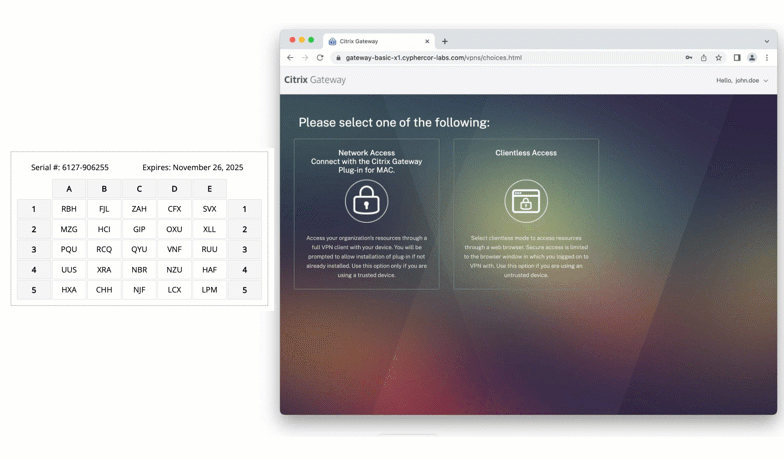
Passcode Grid Authentication with Citrix Gateway
2. Monitoring and policies
LoginTC’s MFA solution allows administrators to apply advanced security policies that limit authentication access based on time of day, geo-location, geo-velocity, and more.
By introducing these automated limits to your authentication environment, administrators are better able to keep track of users’ access attempts without incurring extra work for the help desk team.
Learn more about policies in the video library
3. Logging
Another tool you can use to implement advanced security procedures on your Citrix applications are LoginTC Authentication Logs.
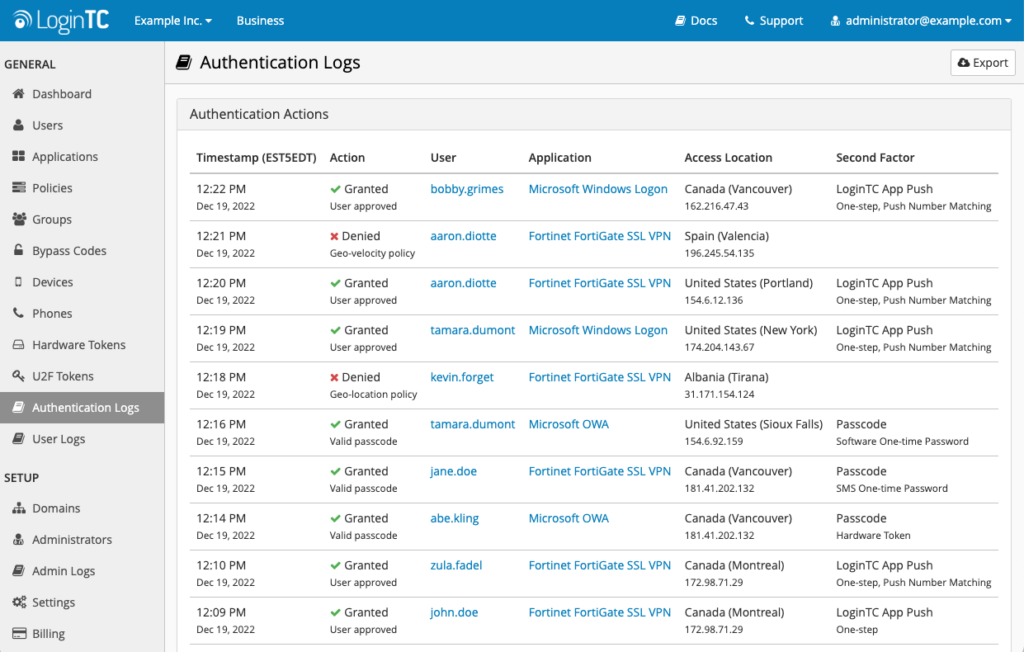
An example of LoginTC Authentication Logs
Administrators can use the authentication log to check for user activity and scan for suspicious activity. Authentication logs show what users logged in when, where, using what authentication method, and into what application. The logs show authentication requests that were approved or denied, giving you a full picture of all access attempts into your organization.
4. Comprehensive coverage
By using LoginTC MFA across your organization, instead of application-based MFA for each of your services, your users need only one token wherever they login.
This allows you to streamline your MFA operations and makes it easier for users to keep track of their authentication credentials, simplifying daily logins for them as well as your help desk team.
Conclusion
While the Citrix Bleed vulnerability has proven to be a significant security threat to countless companies and individuals worldwide, there are preventative measures that can be taken to minimize the risk of exploitation. By understanding how the vulnerability works and implementing the recommended security measures, organizations can better protect themselves against potential attacks.
Now is the best time to consider taking additional measures to protect your organization and its data against breach and theft. LoginTC’s Citrix NetScaler Connector can improve your MFA operations and organization security, without negatively impacting user experience.