How to use MFA to prevent cyber attacks
August 19, 2024 •

As an IT administrator, it’s likely you hear often that MFA can be used to prevent cyber attacks. You may be wondering if that is true, and how it works.
In this article, we’ll go through what MFA is and some notable stories of when cyber attacks could have been prevented with MFA. By the end of this article, you’ll better understand how MFA stops cyber attacks and how to implement MFA at your organization.
Let’s dive in.
Table of Contents
- What is Multi-factor Authentication?
- How does MFA stop cyber attacks?
- When could MFA have prevented cyber attacks?
- When has MFA prevented a cyber attack?
- How to use MFA to stop cyber attacks
What is multi-factor authentication (MFA)?
Multi-factor authentication is the process of gaining access to an account or system by proving identity through more than one factor.
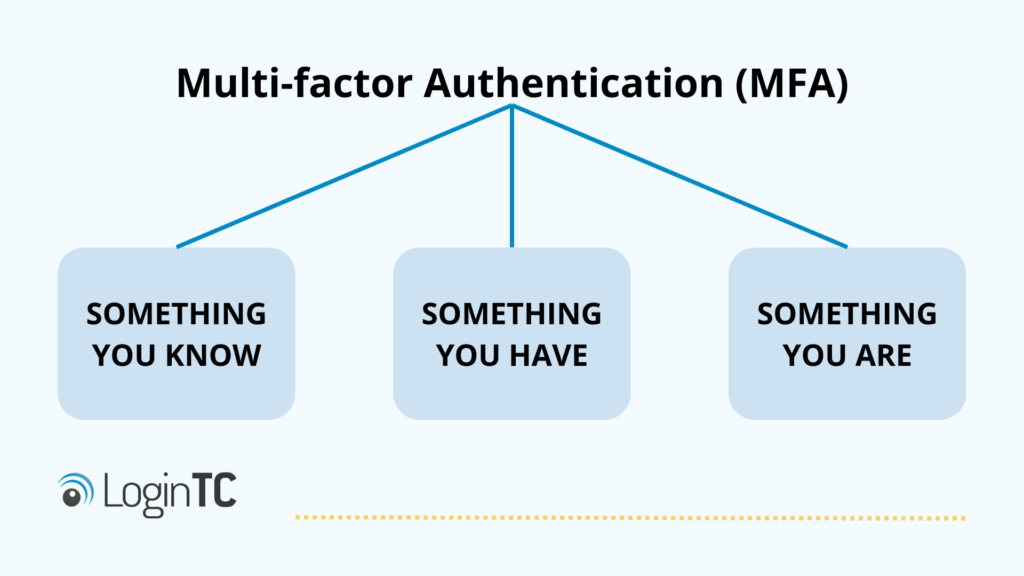
Identity factors fall into three categories:
- Something you know (a password, security questions)
- Something you have (a hardware token, a smartphone with authenticator app)
- Something you are (biometrics)
Accounts that have MFA enabled require a combination of these factors to be provided by the individual before access is granted.
How does MFA stop cyber attacks?
When password-only authentication is implemented on accounts, then the account is only as strong as the password protecting it. However, when multiple identity factors are required to login, then even if a password is weak or has been compromised, an attacker will not be able to access the account.
For example, if an administrator’s password to their VPN login has been compromised in a data breach, a potential threat actor can try to login remotely using their email and leaked password. Say that account also has a second-factor authentication challenge using a software token on an authenticator app, the attacker will not gain access to the account, as they don’t possess the token.
Furthermore, the administrator is now made aware that an access attempt was made by a third party, and can take necessary steps to prevent further attacks.
When could MFA have prevented cyber attacks?
Many cyber attacks that have made major news over the past few years could have been prevented if the compromised accounts had implemented MFA.
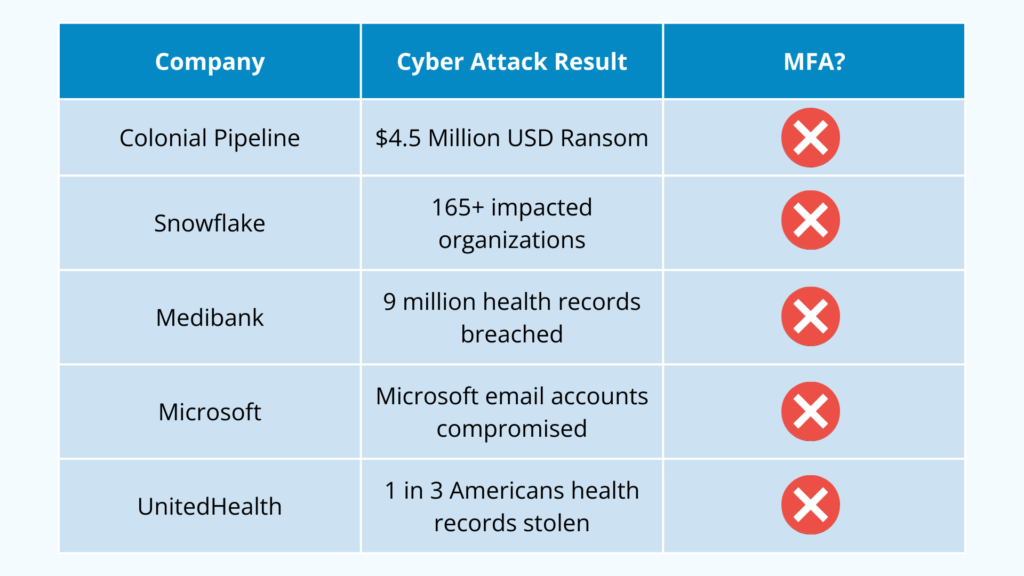
Let’s take a look at a few of them below.
Colonial Pipeline
The Colonial Pipeline attack happened in May of 2021 and impacted the oil supply to the northeastern United States for an entire week. The company paid a $4.5 million USD ransom to regain control over their systems.
The attackers used a compromised employee password to gain access to a VPN account that did not have MFA enabled. An investigation later revealed that the password had been leaked from a previous data breach, which was found on the dark web.
Snowflake
Snowflake, a major cloud data warehousing company, was implicated in several data breaches that occurred in 2024. Snowflake account settings limited the ability for administrators to enforce MFA policies on accounts.
This weakness led to several companies being breached, including Santander Bank, Ticketmaster, and AT&T. As the responsibility for enabling MFA on accounts fell to end-users, attackers were easily able to gain access to accounts with large amounts of data that hadn’t enabled MFA.
Medibank
Medibank, a large Australian private health insurer, was breached in 2022 and the private information of over 9 million people was compromised and released online.
The attack occurred after an IT administrator’s computer was infected with malware, giving attackers access to Medibank usernames and passwords, including drives where the data was hosted.
The accounts did not have MFA enabled, so once the attackers had acquired and tested the first factor credentials, they had full access to the sensitive data.
Microsoft
In November of 2023, the Midnight Blizzard hacking group was able to access a section of Microsoft’s corporate environment and targeted Microsoft email accounts.
The attackers gained access using a ‘password-spraying’ tactic against a legacy test account. The account in question did not have MFA enabled, so the attackers only needed to gain access to the password and username to compromise the accounts.
UnitedHealth
In February of 2024, UnitedHealth was breached by a ransomware gang, which stole six terabytes worth of data, including the sensitive medical information of an estimated 1 in 3 US residents.
The attackers were able to gain access to the data through a server that did not have MFA-protected logins.
UnitedHealth paid a $22 million USD ransom to regain access to their accounts and prevent the data from being leaked, but despite this the customer data has appeared on the dark web in the months following the breach.
What about cyber attacks against smaller businesses?
The reality is, despite the fact that most news stories are about large companies being the victims of cyber attacks, it’s small to medium sized businesses that have the most to worry about.
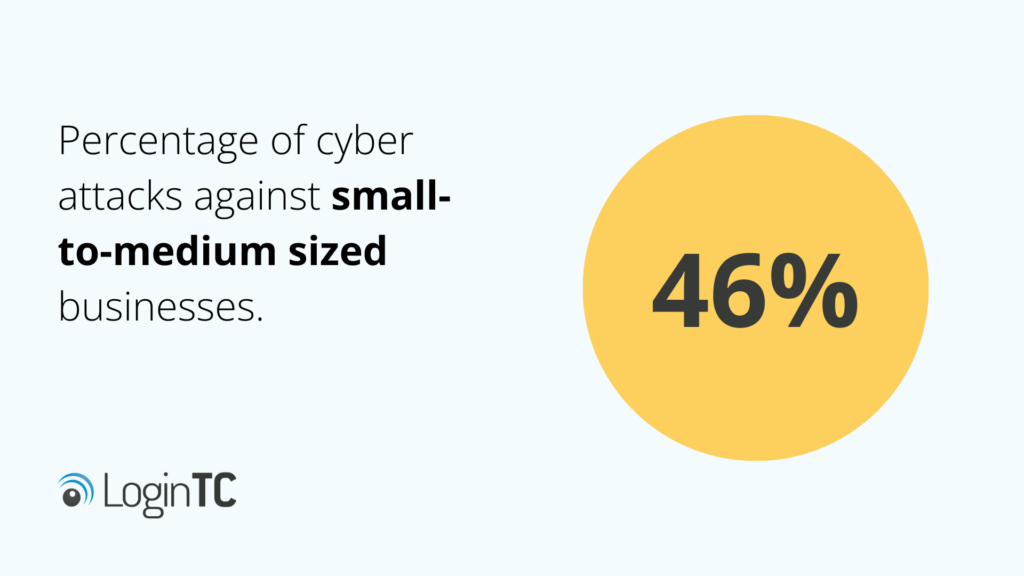
Verizon’s 2021 Data Breach Investigation report found that 46% of data breaches were against small to medium sized businesses. The report also found that these attacks can cost small businesses anywhere from $826 USD to more than $650,000 USD.
When has MFA prevented a cyber attack?
Good news stories rarely make the news, but luckily we have an example of when MFA prevented a cyber attack.
In September of 2022, a hacker gained the password credentials of an executive at a large law firm in Connecticut through a successful phishing attempt. However, when the attacker tried to login to the company’s remote access systems using the newly gained credentials, they were unable to. MFA had been enabled on the account, and since the attacker didn’t have access to the second factor credentials, they were locked out of the account.
The unusual activity was flagged quickly and the user’s password promptly changed.
If successful, the attack would have resulted in 30,000 individuals’ information being leaked, and cost the company over $7 million USD in credit monitoring fees alone. When factoring in recovery costs, business interruption, ransomware payments, insurance premium increases, and more, the law firm would’ve faced losses of over $10 Million USD.
How to use MFA to stop cyber attacks at your organization
Implementing MFA at your organization to prevent cyber attacks isn’t always a one-and-done process.
As an IT admin responsible for cybersecurity, you have to consider all the possible areas where MFA needs to be implemented in order to have a full MFA deployment.
Let’s take a look at some of the key areas where MFA can protect your organization below.
MFA for Remote Access
MFA is commonly recommended for all remote access functions.
As remote access has become more popular, especially with the expansion of remote working, it is easier than ever to login to account from anywhere in the world. However, it is also easier for malicious actors to gain unauthorized access, as they no longer need to be physically in the same location as the device they’re trying to access.
If you’re looking to expand your MFA coverage, remote access is a good place to start.
MFA for VPNs and Firewalls
VPNs and firewalls allow companies to channel traffic through secure, private networks. But they too must be protected from unauthorized access, otherwise the traffic could be intercepted.
Your organization should consider adding MFA to your company VPN. Whether you use Citrix, SonicWall, Watchguard, Fortinet, or any other LDAP and RADIUS-speaking applications, MFA can add the additional security a VPN needs.
MFA for Privileged Access
How many times are companies breached because accounts with the highest possible access were not protected properly?
Ensuring your privileged users (also known as administrators, or root users) have MFA enabled on all points of access can help your organization prevent cyber attacks like the ones mentioned in this article.
MFA for Email
Business email compromise is a popular way for attackers to breach systems. Beyond the initial data trove it provides, attackers use compromised email accounts to send realistic phishing emails and compromise more accounts.
By implementing MFA on email accounts such as Outlook Web App, you can prevent malicious actors ever gaining access to your corporate emails.
MFA Anywhere
Today, there’s almost no limit to what you can protect with MFA.
A comprehensive MFA deployment may feel time consuming and costly, but the alternative is far worse. From terabytes of data lost, to ransomware payments, to massive business interruptions, the cost of cyber attacks is far greater than the cost of cybersecurity controls.
If you’re not sure where to start with MFA, check out the MFA Gap Calculator. In a few minutes, you’ll receive a report in your inbox that includes a detailed list of areas where your organization needs MFA, and how to take action.