How to use offline MFA for Windows Logon
August 27, 2024 •
This blog series showcases a variety of common and unique authentication scenarios, and recommended authentication solutions for each.
This installment explores three different authentication scenarios where offline MFA with Windows Logon is needed, as well as the six different solutions for these use cases. Check out one of our previous blogs about offline authentication with Windows Logon if you’re interested in learning more.
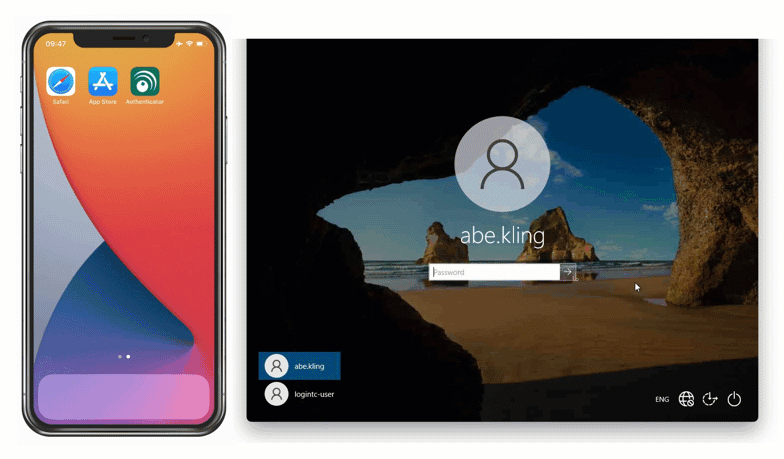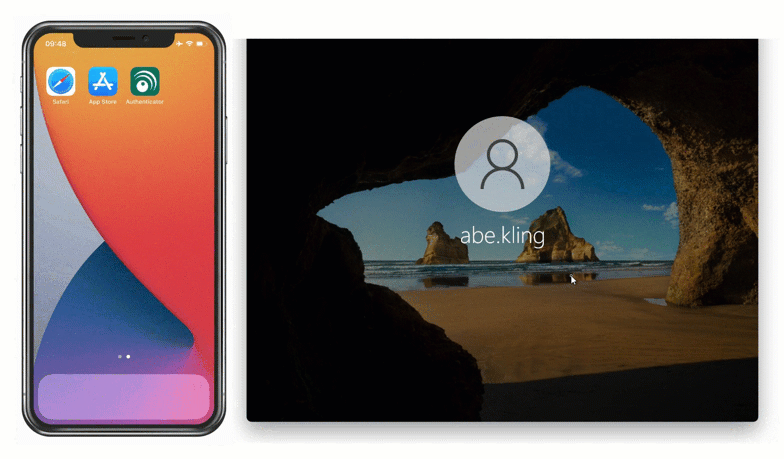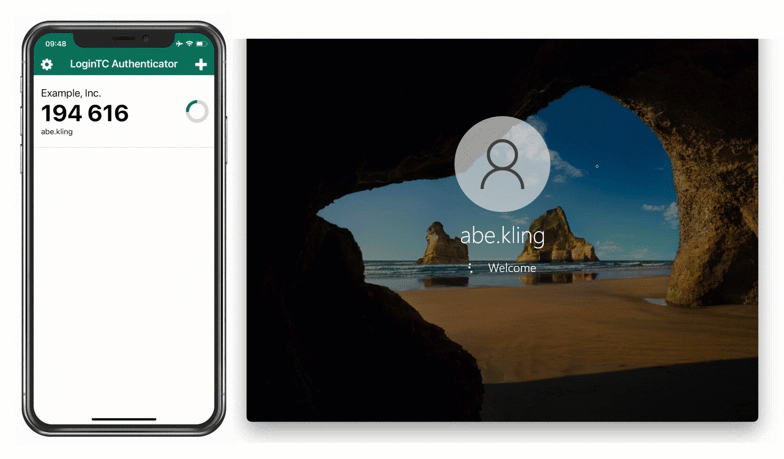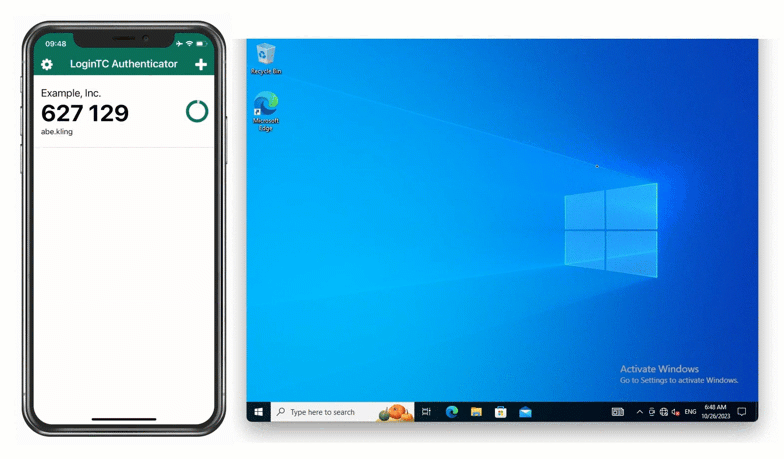
Scenario One: Offline Authentication with Smartphone

Maria is an employee at a software company, who occasionally has to travel on business to conferences and trade shows. She has a company issued smartphone and uses it with the LoginTC app for second factor authentication when logging into Windows Logon.
One day she arrives at a conference and wants to show one of her business partners a demo of her company’s product, but Maria’s laptop can’t connect to the conference hall Wi-Fi until she logs in.
How can Maria login to her laptop without first being connected to the internet?
Solution: Offline QR Code
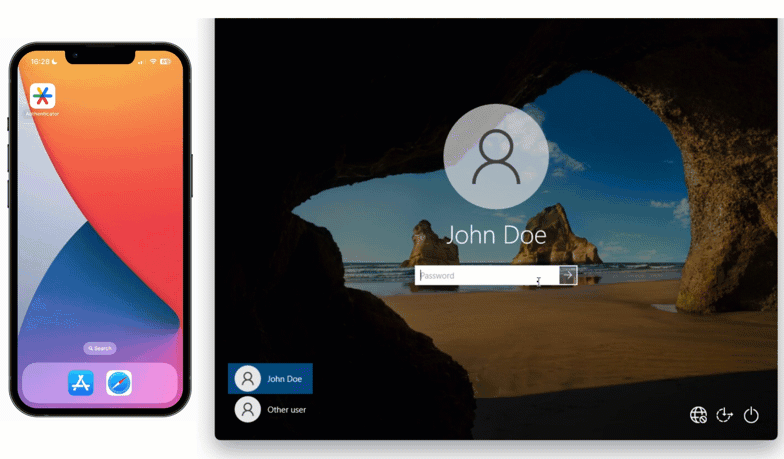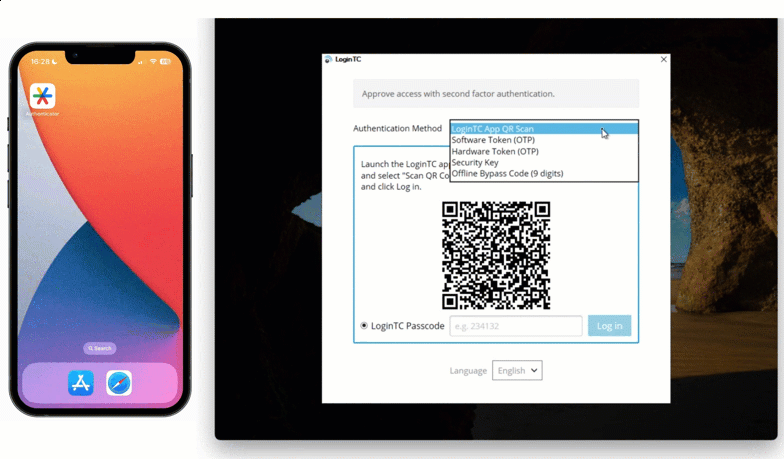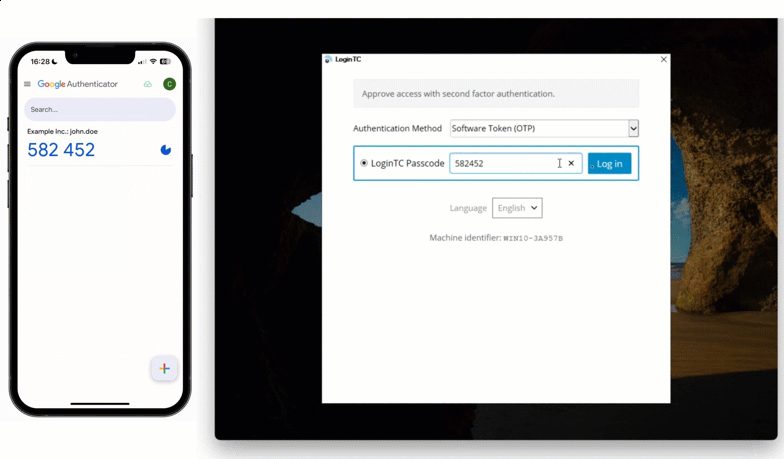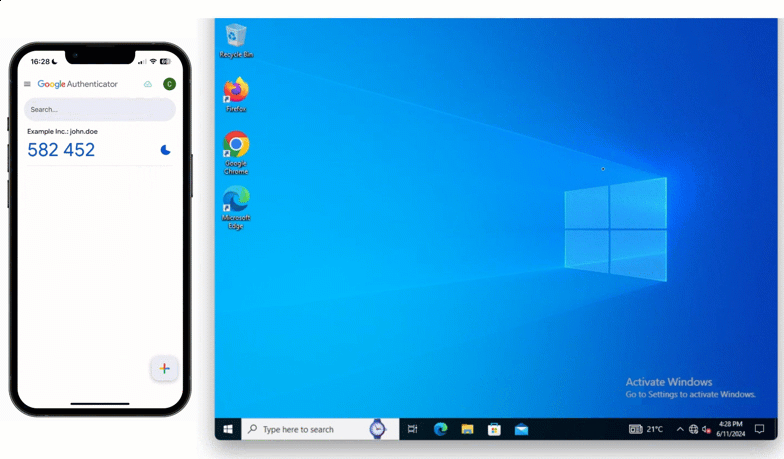
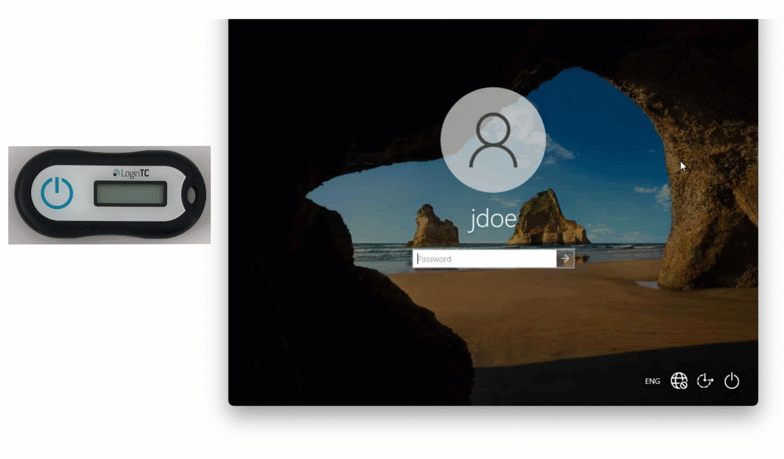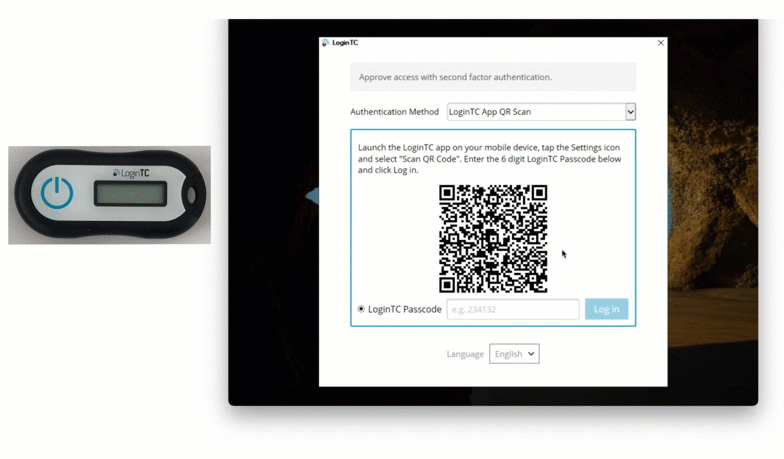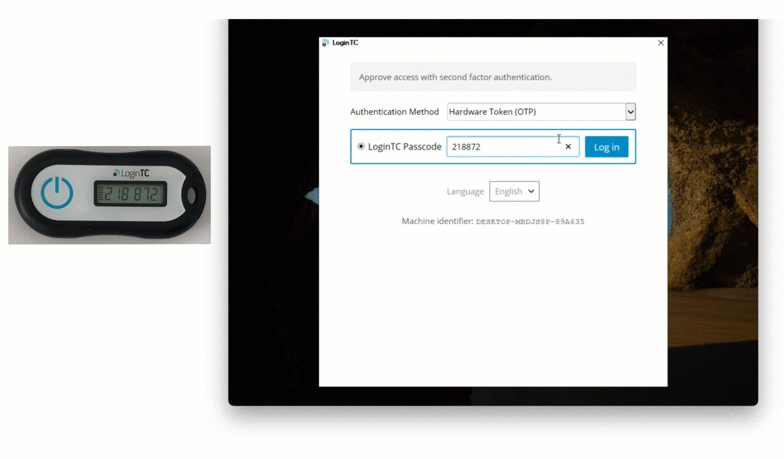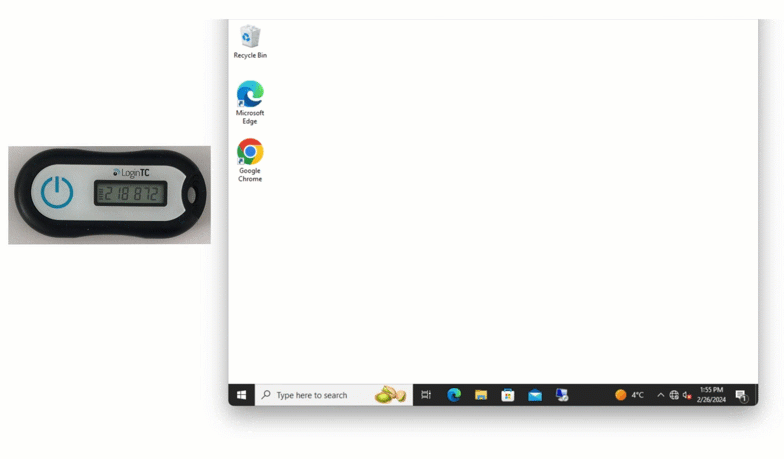
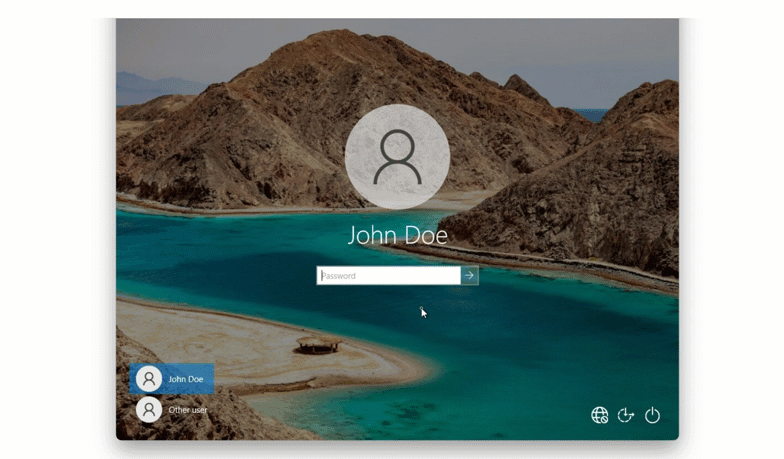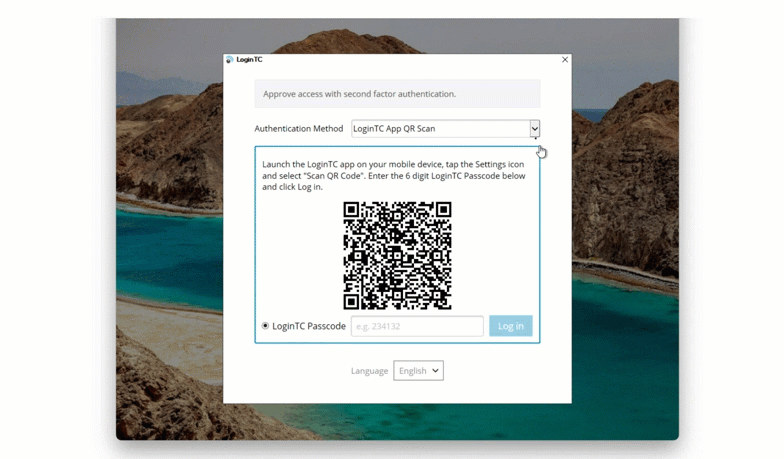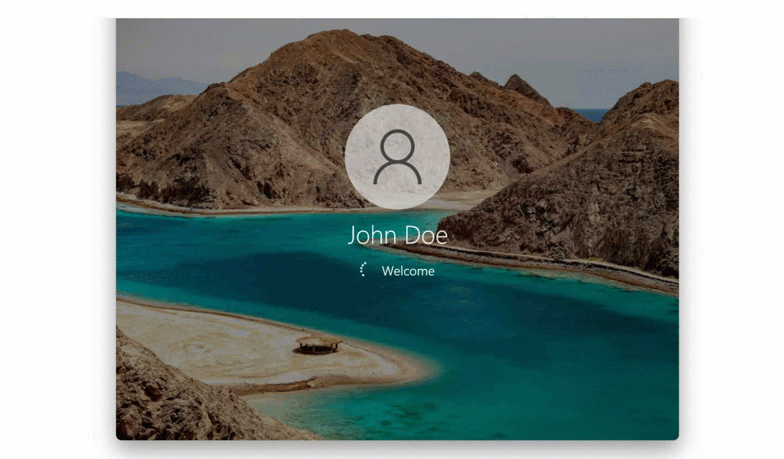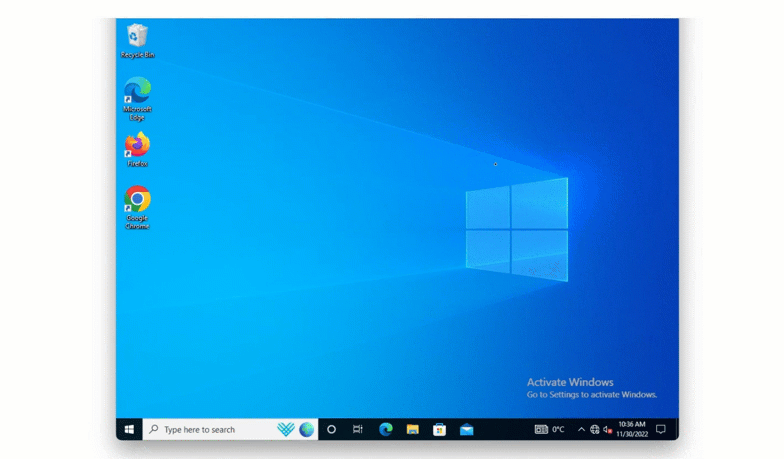
In order to facilitate offline authentication, Maria’s IT team has set up Offline QR Code. This authentication method utilizes a QR code to generate one-time passwords in an authenticator app.
To use this method, Maria inputs her first factor credentials into her Windows machine and then selects “LoginTC App QR Scan” from the dropdown list of authentication methods. She opens her LoginTC app and selects “Scan QR Code”. This opens up the camera in her LoginTC app, and Maria can use her phone to scan the QR code shown on her computer. This generates a one time password in the app, which Maria inputs into the space provided.
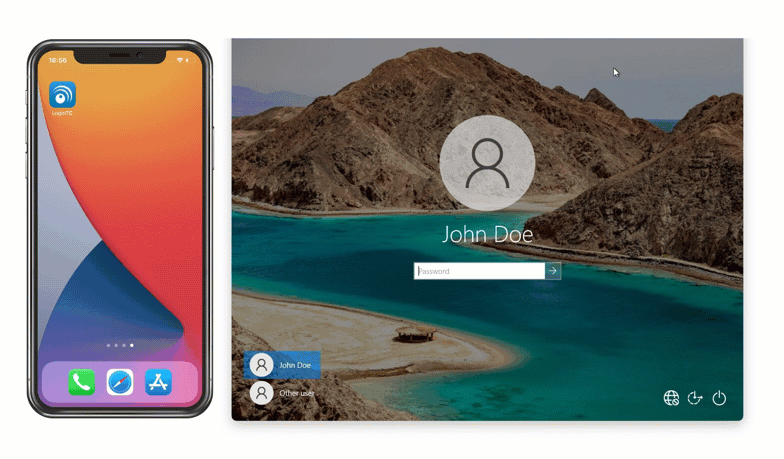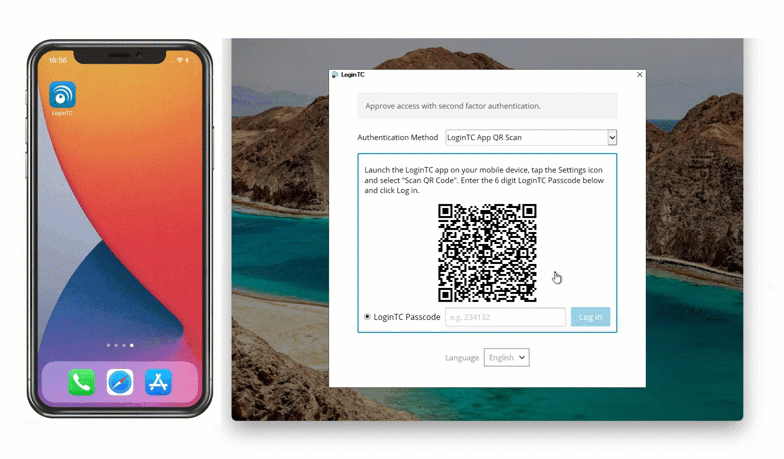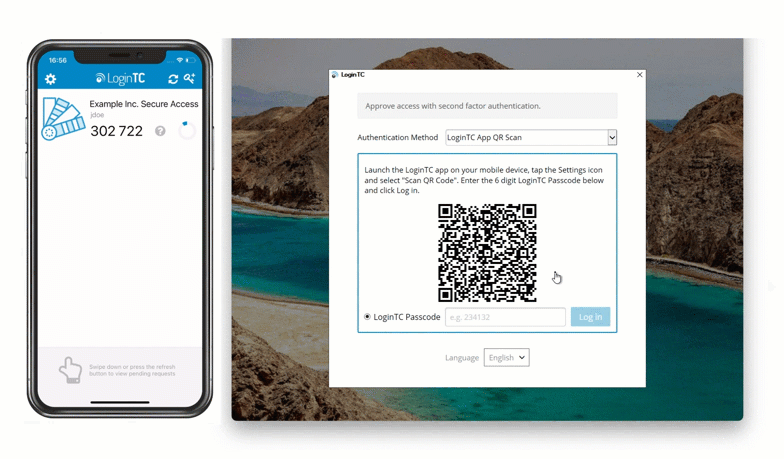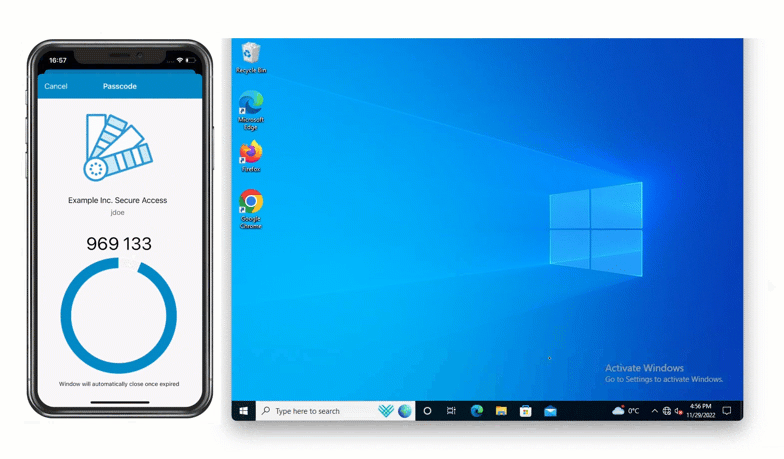
She’s now securely logged in to her Windows machine with zero external communication required.
Solution: Third-party Authenticator App
Maria’s company could also allow end-users like her to use a pre-existing authenticator app, like Google Authenticator or Microsoft Authenticator, that Maria is already familiar with.
To use this method, Maria inputs her first factor credentials into her Windows machine and then selects “Software OTP” from the dropdown list of authentication methods. She opens her authenticator app, and inputs the 6-digit code into the space provided.
This method means Maria doesn’t need to download additional authenticator apps onto her device, and her company can still take advantage of LoginTC’s advanced functionality.
Solution: Offline Software Token
Maria’s company chooses to start using a fully on-premises authentication solution, such as LoginTC Managed. Included in this solution is an authenticator app that can generate one-time passcodes with zero external network connectivity required.
Maria uses this app to login to all of her protected services and applications. After inputting her first factor credentials, she selects “Software Token OTP” from the dropdown list of available methods and inputs the 6-digit code into the space provided.
Scenario Two: Offline Authentication without Smartphone

James works in a high-security environment for a company that builds and operates solar farms. To protect internal systems, external network connectivity is strictly prohibited. His company does not issue company smartphones to all staff.
To secure these systems, James’ company is introducing multi-factor authentication (MFA), but they want to ensure that no external connections are required for authentication and that smartphones are not used for authentication.
Solution: Passcode Grid
James’ IT team decides to implement Passcode Grid authentication for every employee at the company.
A passcode grid is a 5×5 grid with cells containing 3-character tuples. This grid is unique to James, and he can print out the passcode grid, or save it somewhere secure.
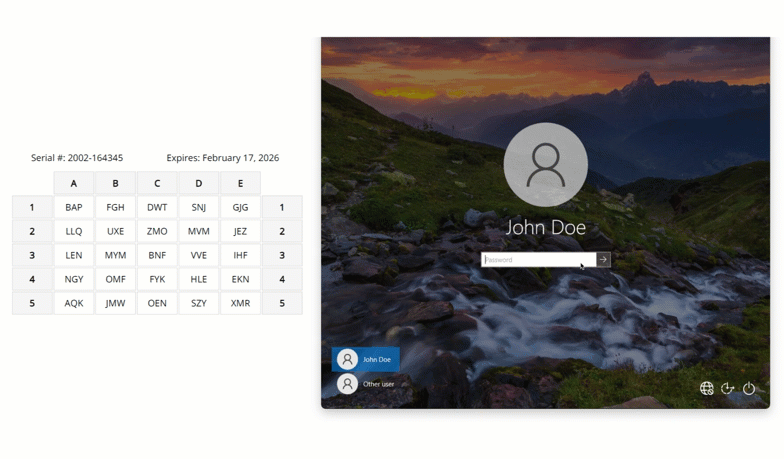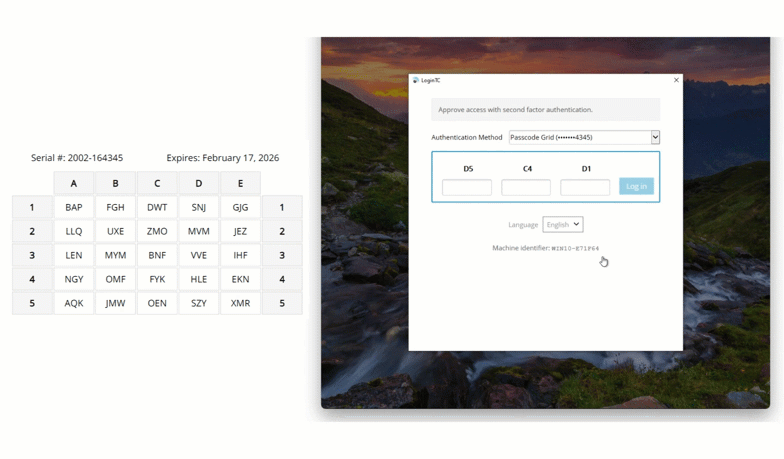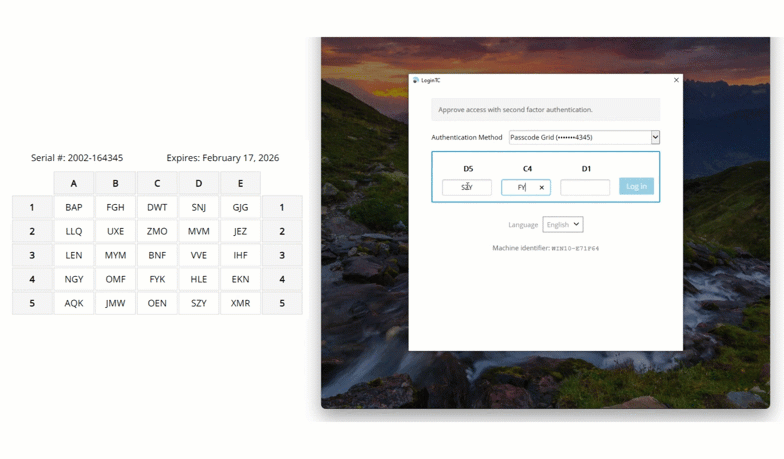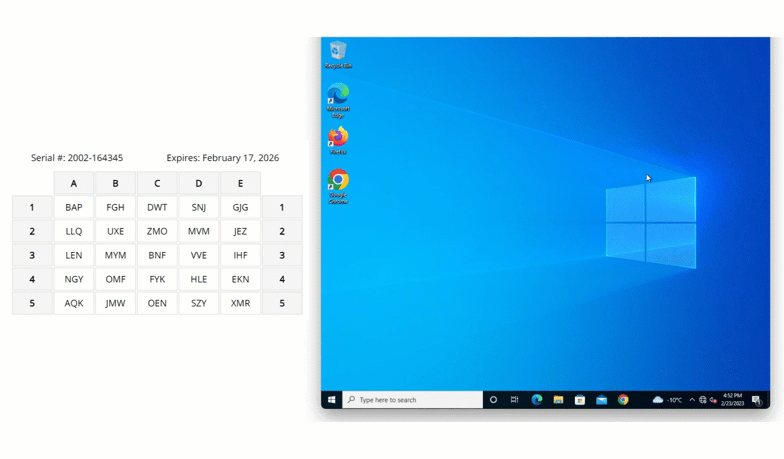
James logs into his Windows machine with his first factor credentials, and when prompted, selects “Passcode Grid” from the list of available authentication methods. Then in the spaces provided, James inputs the requested tuples and clicks “Log in”.
If James’ company switches to an on-premises MFA solution, a passcode grid can also be used for offline authentication with an on-premises deployment.
Solution: Hardware Token
James’ company could also choose to distribute hardware tokens to each employee for use both offline and online. Hardware tokens are physical authentication devices that generate 6 or 8-digit one time passwords.
After inputting his first factor credentials, James can select Hardware Token from the dropdown list, tap the button on the hardware token, and type in the number shown. This method can also be used with an on-premises deployment.
Solution: Security Key
Another way that James’ company can provide non-smartphone based offline authentication is using a Security Key. FIDO2 Security Keys offer strong, phishing-resistant authentication while being easy to use.
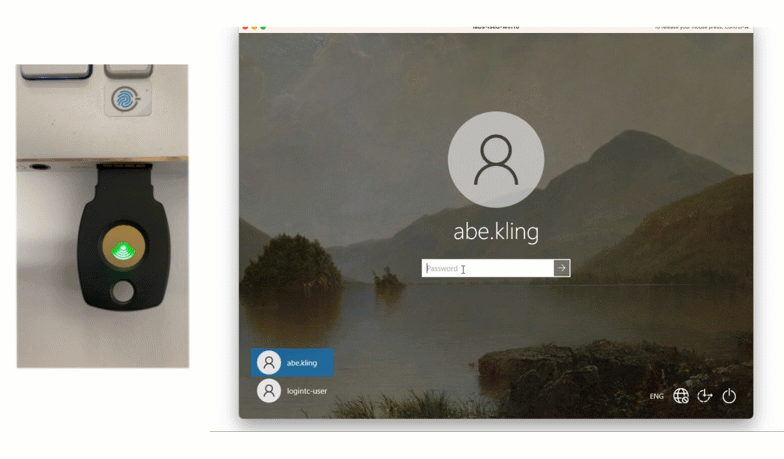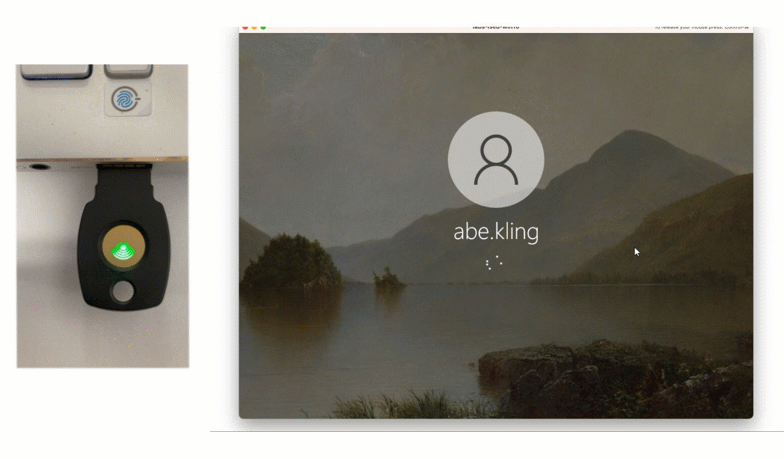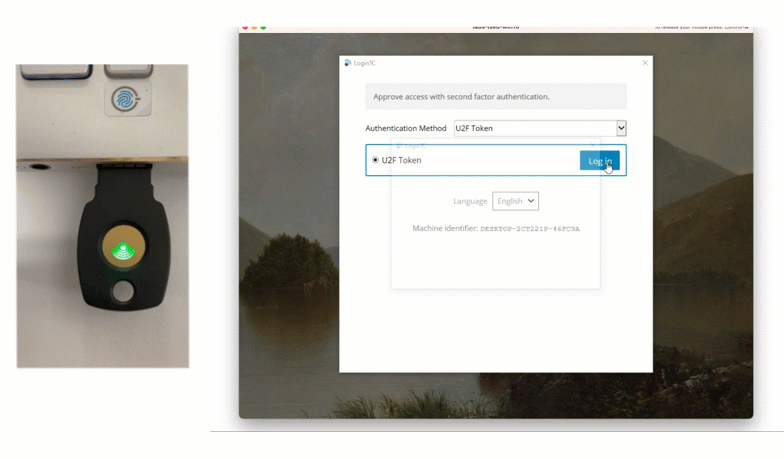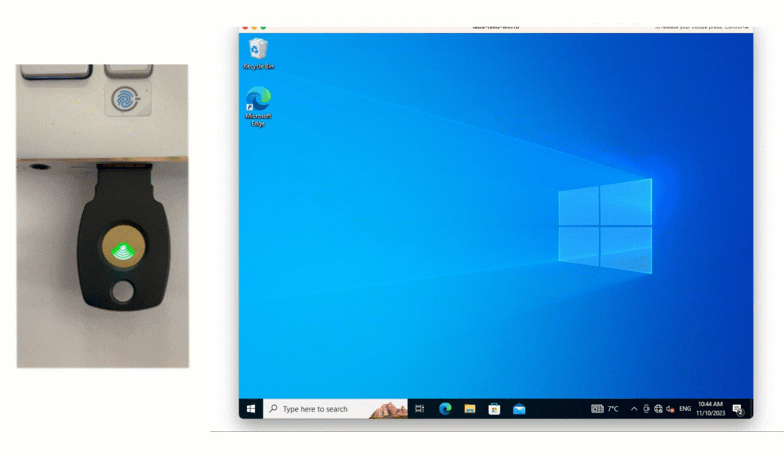
To use this method, James can select Security Key from the authentication drop down list, insert his security key, and simply tap the button to authenticate. This method is also available with an on-premises deployment.
Scenario Three: Emergency Offline Authentication

Philippe is on his way to a company retreat when his connecting flight gets canceled, and his bags are lost in transit. He needs to let his team know that he’s going to be late, but his company doesn’t allow for smartphone authentication, and his passcode grid is in his checked luggage.
How can Philippe log into his laptop to send an email to his team?
Solution: Offline Bypass Code
Philippe calls his company’s help desk, who instructs him to use an offline bypass code.
Philippe logs into his laptop with his username and password and, recognizing that he is not connected to the internet, the system prompts him for an offline bypass code. Philippe’s help desk relays the 9-digit code to him from where it’s listed in his user account, and he inputs the code to complete login.
Philippe can now find a secure Wi-Fi connection and get an email to his team.
Conclusion
Whether you need users to be able to authenticate offline with or without a smartphone, or in an emergency, there’s an authentication solution for your use case.
Explore every LoginTC authentication method, and stay tuned for the next installment of our authentication use case series.