Stop Brute-Force Attacks: LoginTC RADIUS Connector Adds IP Address Blocking
February 13, 2025 •
The LoginTC RADIUS connector is an MFA solution that secures all RADIUS-speaking VPNs, firewalls, switches, routers and more. Our latest update adds critical security upgrades that will help keep malicious actors trying to gain unauthorized access to your network.
Let’s explore the latest update below.
IP Address blocking
Brute force attacks use repeated login requests to overwhelm and force entry into systems and applications, such as VPNs and firewalls. Multi-factor authentication (MFA) can keep these would-be attackers out by enforcing strong authentication security.
In addition to preventing successful logins, LoginTC MFA can now also stop access requests with our new feature: IP Address blocking.
Blocking criteria
- Log into the LoginTC RADIUS Connector web based interface
- Go to Endpoints
- Click your endpoint
- Scroll down to Client Settings, click Edit
- Scroll down to Blocked Failed Logins, select Yes, block IP Addresses with consecutive failed logins
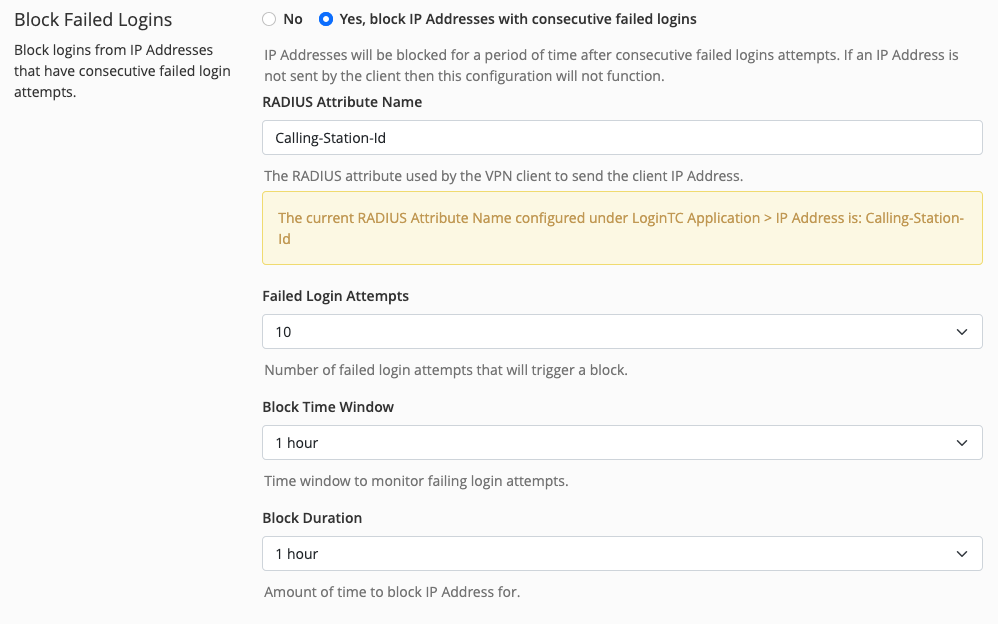
- Select desired options
- Scroll down, Click Test and Update
The IP address blocking features allows administrators to automatically block IP addresses that meet certain criteria. IP address blocking allows you to set:
- How many times an IP address can fail to login before triggering a block.
- What the time window is for failed login attempts.
- How long that IP address will be blocked for.
This customization allows administrators to determine how IP address blocking operates in their system. This ensures administrators remain in full control over how their VPNs and firewalls function.
The originating connection’s IP address is provided by the upstream RADIUS client via a RADIUS attribute, typically Calling-Station-Id. This attribute is configurable; for example, Palo Alto Networks firewalls use PaloAlto-Client-Source-IP instead.
Data visualization
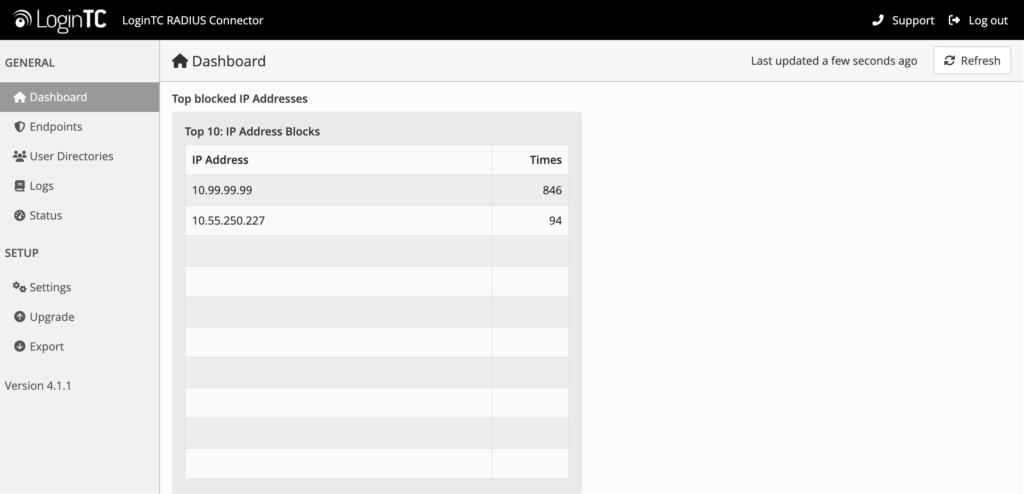
When the Block IP addresses feature is enabled, a list of Blocked IP addresses will appear in the Dashboard stats section of the LoginTC RADIUS Connector.
The table shows a list of the top 10 IP addresses that have been blocked sorted by how many times they attempted to access the application.
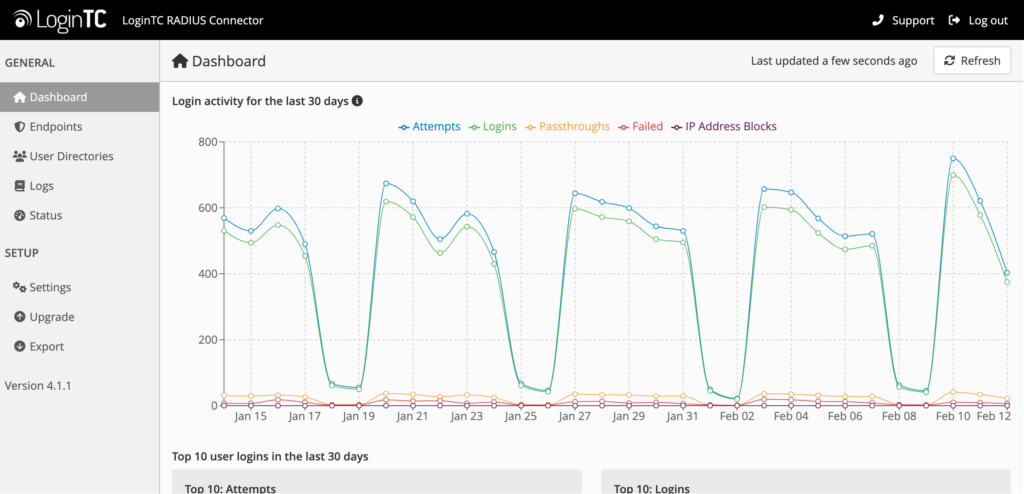
Blocked IP address data will also appear in the login activity graph at the top of the Dashboard page.
These tables and graphs make it easy for administrators to quickly see the impact of blocked IP addresses and investigate any security events.
Best practices
The IP address blocking feature is designed to work with your organization’s particular needs.
In our tests, we’ve found that login failures of 5-10 attempts in under 5 minutes likely represent bot activity, rather than genuine end-user error. Blocking these attempts for 12-24 hours is a good starting configuration of this feature, which allows you to further investigate the cause and source of this suspicious activity.
Note that toggling the IP address blocking feature off and then on again will reset all blocked IP addresses. Additionally, rebooting the appliance also unblocks all IP addresses.
MFA Security Innovation
LoginTC is the first MFA solution known to offer this security feature.
This feature allows administrators to block IP addresses even if your VPN, firewall, or RADIUS endpoint does not offer the same capability.
This innovation is just one more reason to choose LoginTC for your MFA solution.
Get the latest RADIUS Connector update today
The IP address blocking feature is available right now in your LoginTC RADIUS Connector. Make sure you have access to the latest features in the RADIUS connector by upgrading to 4.1.1.
If you want next-level MFA security for your organization, try LoginTC free today.