Last Updated: March 27, 2025
The LoginTC RD Web Access Connector protects access to your Microsoft Remote Desktop Web Access by adding a second factor LoginTC challenge to existing username and password authentication. The connector protects both web and RemoteApp web feed access, and works in conjunction with the LoginTC RD Gateway SSO Connector to provide a seamless and protected Remote Desktop experience.
If you would like to protect just your RD Gateway without protecting RD Web Access then you may be interested in the: LoginTC RD Gateway with RADIUS Connector.
Subscription Requirement
Your organization requires the Business or Enterprise plan to use the LoginTC RD Web Access Connector. Explore Pricing Plans
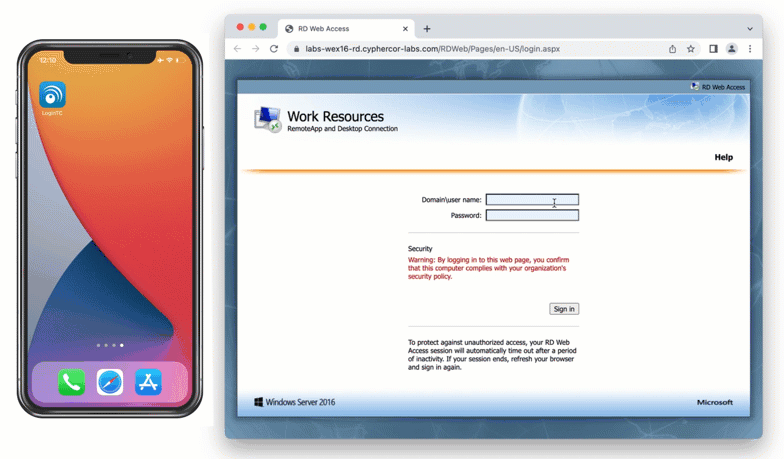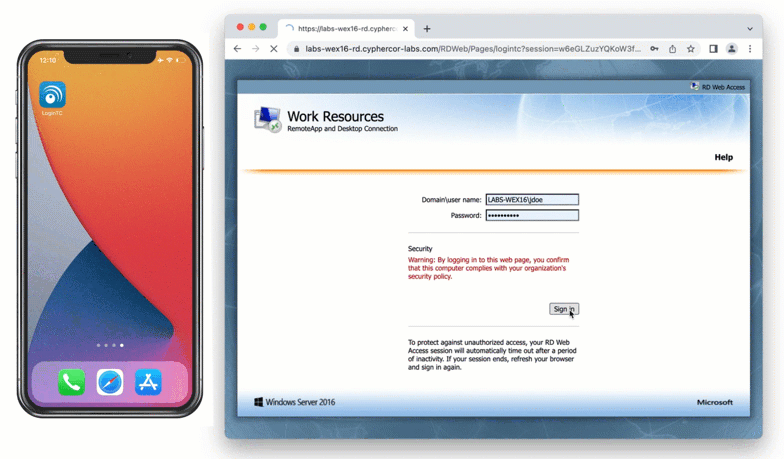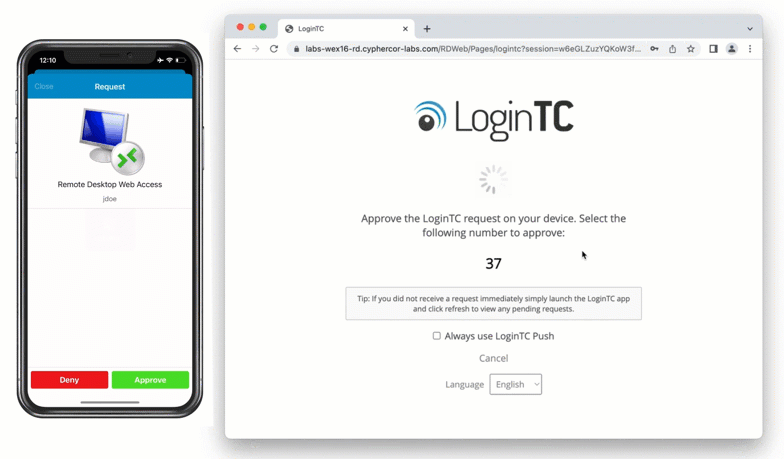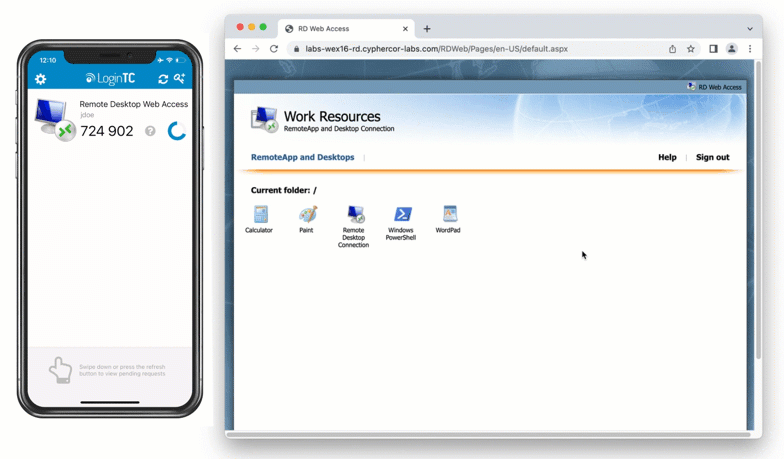
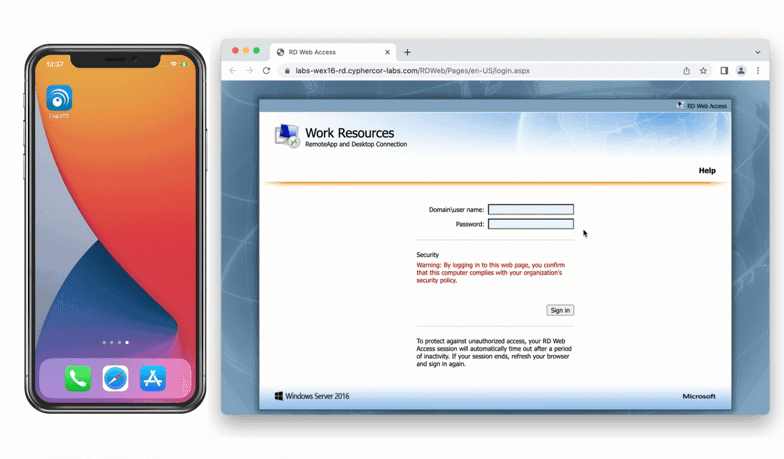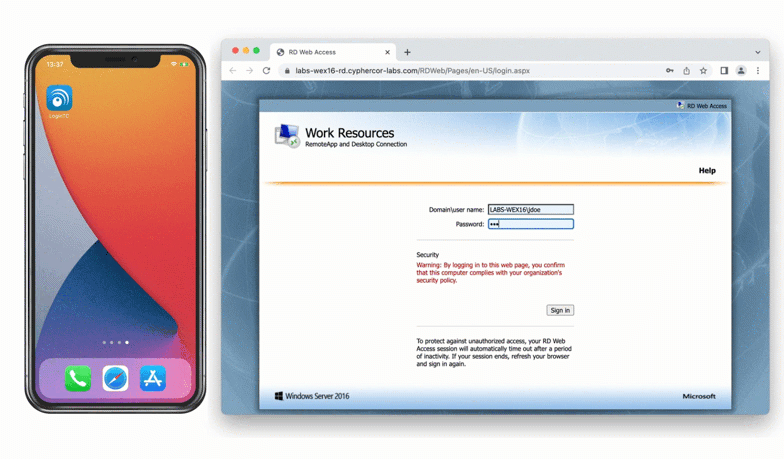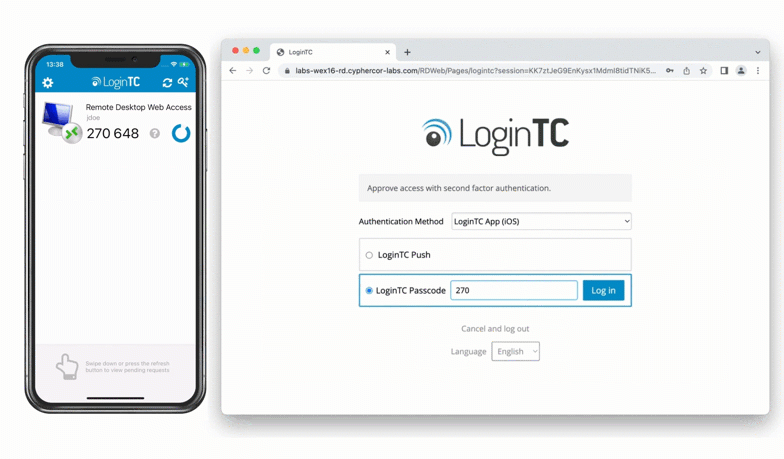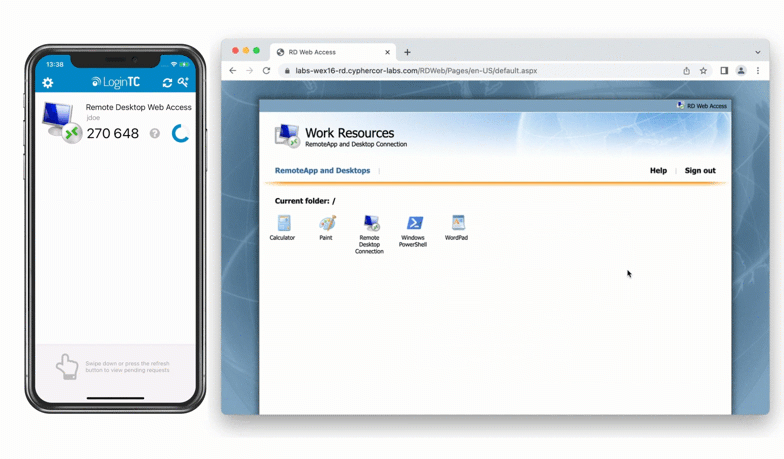
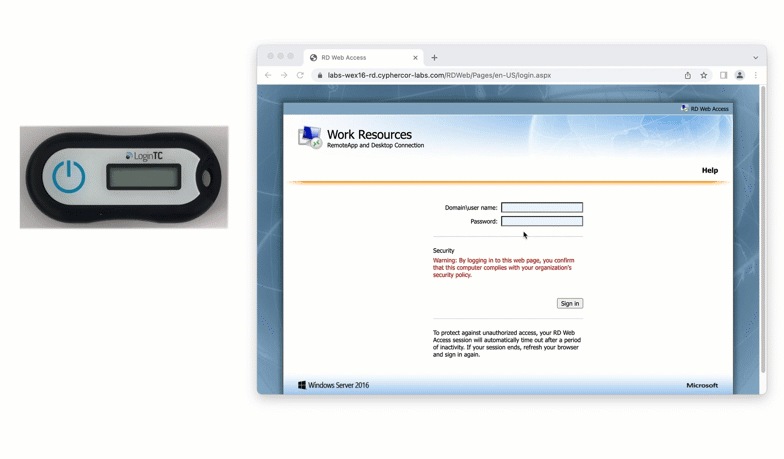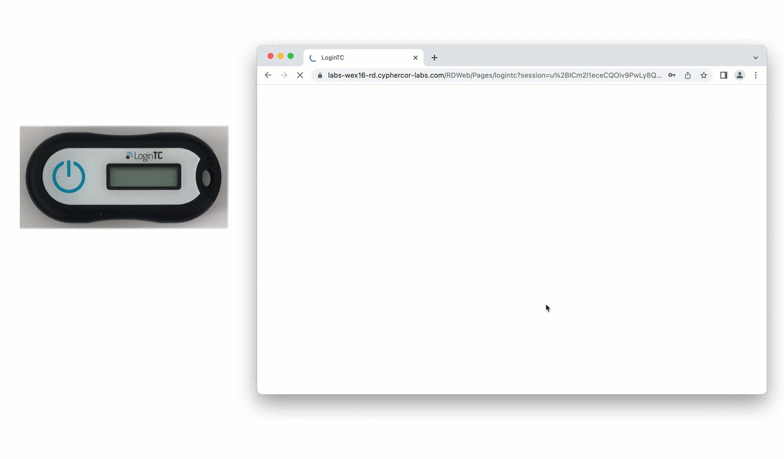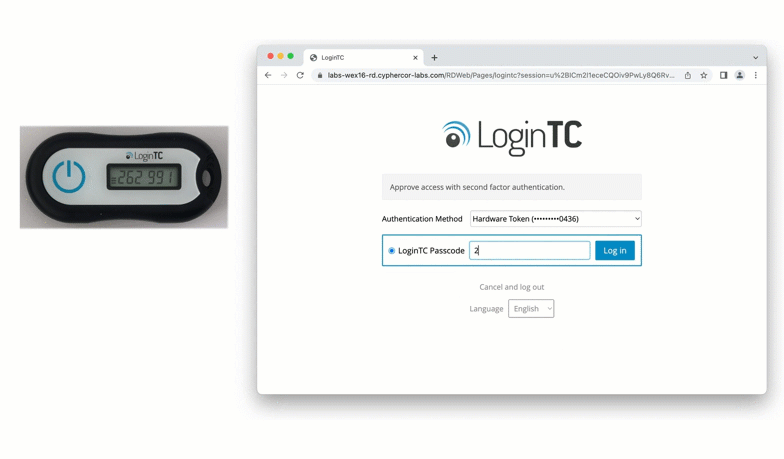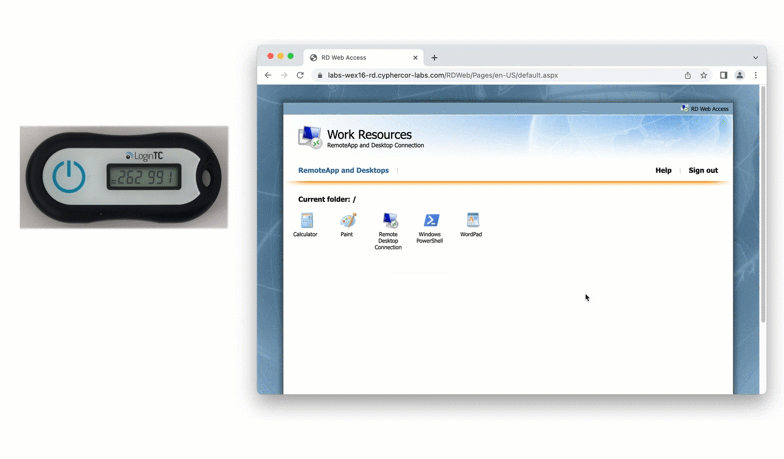
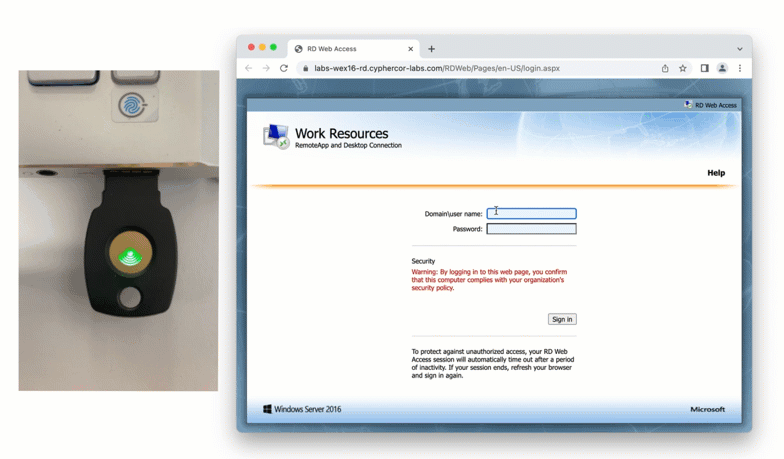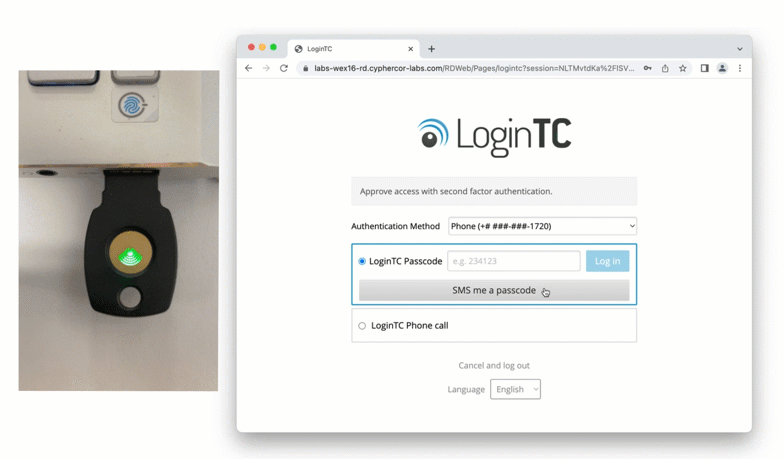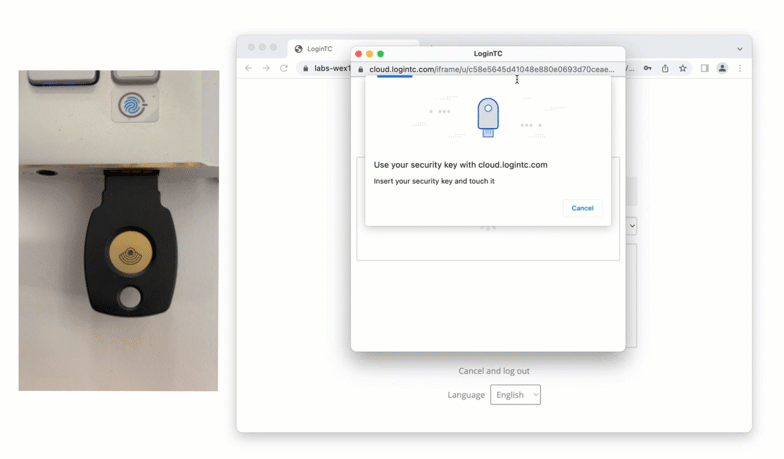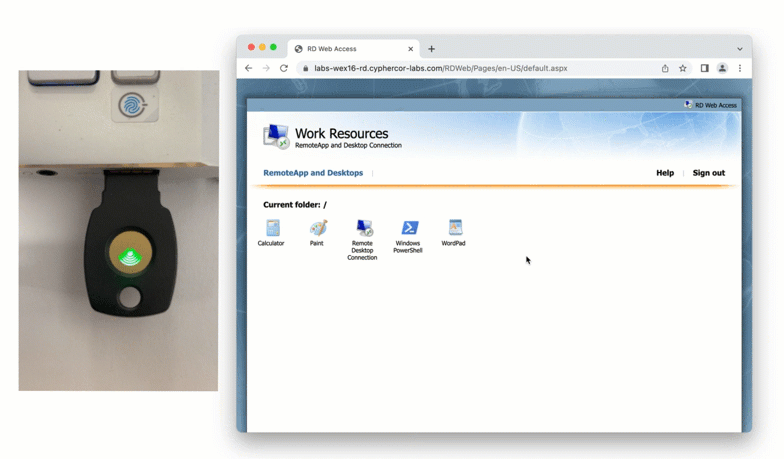
After entering the username and password into the RD Web Access login, the user is shown a selection of second factor options. The user clicks a button to receive a LoginTC push notification, authenticates and is logged in.
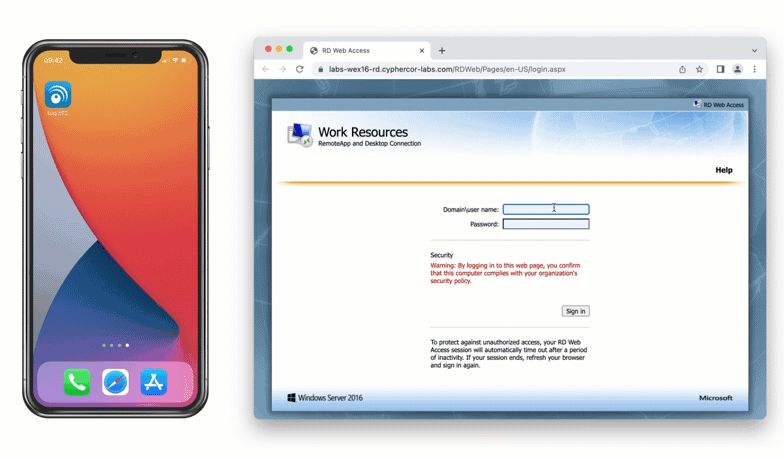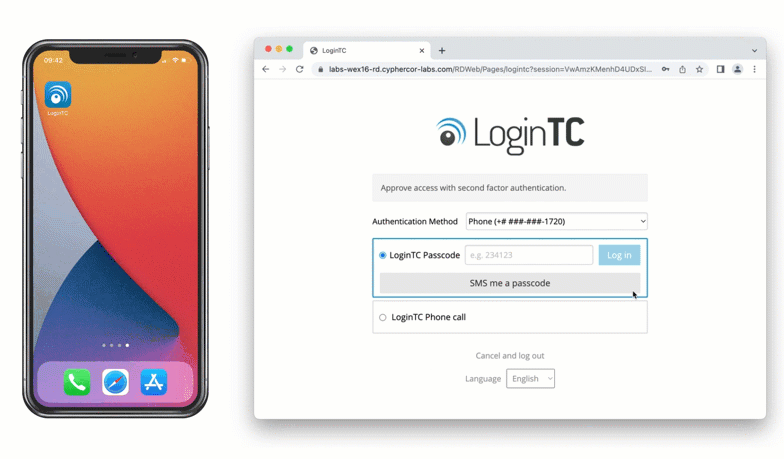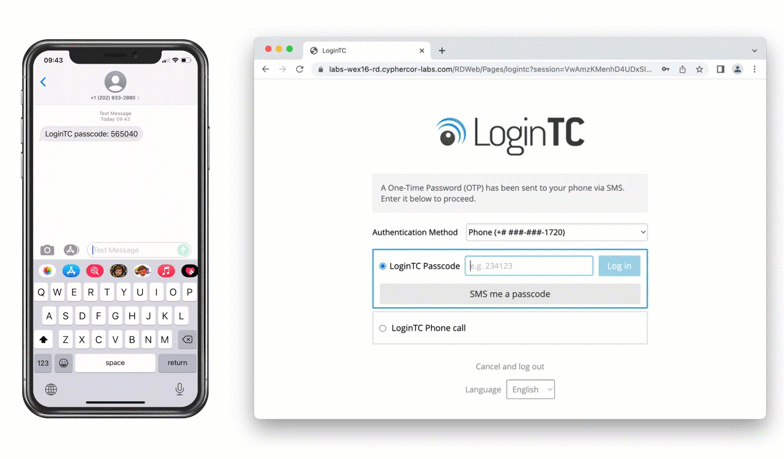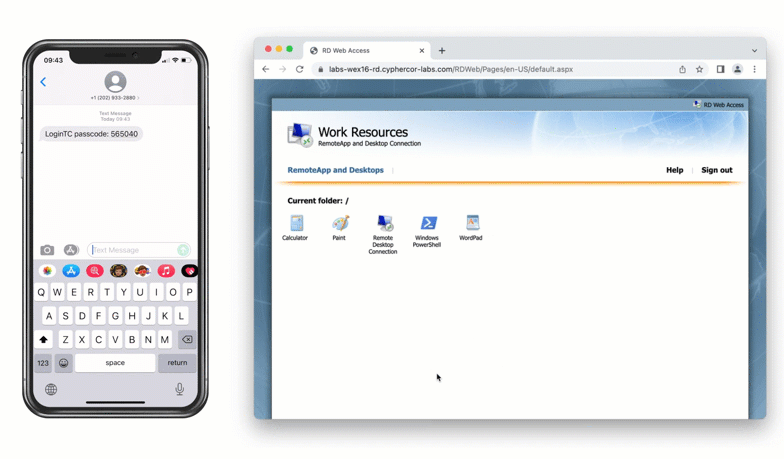

Authentication Flow
- A user attempts access to Remote Desktop Web Access with username / password
- The username / password is verified against an existing first factor directory (i.e. Active Directory)
- The request is trapped by LoginTC RD Web Access Connector and an authentication request is made to LoginTC Cloud Services
- Secure push notification request sent to the user’s mobile or desktop device
- User response (approval or denial of request) sent to LoginTC Cloud Services
- The LoginTC RD Web Access Connector validates the user response
- User is granted access to RD Web Access portal
- User clicks on one of the available applications / remote desktop sessions from the portal
- The RDP file connects with Remote Desktop Gateway
- The LoginTC RD Gateway Connector validates the RDP file and the user is granted access to remote resource
Prefer Reading a PDF?
Download a PDF file with configuration instructions:
Before proceeding, please ensure you have the following:
- LoginTC Admin Panel account
- Microsoft Windows Server 2012 R2, Windows Server 2016, Windows Server 2019 or Windows Server 2022
- Remote Desktop Web Access role
- Remote Desktop RD Gateway role (may be on the same host as the RD Web Access role)
- Working Remote Desktop Web Access Deployment
- .NET Framework 4.5.2 or higher
Working Remote Desktop Web Access Deployment
It is strongly recommended that you have a working and tested Remote Desktop Web Access deployment prior to adding LoginTC authentication.
Start by creating a LoginTC Application for your deployment. An Application represents a service (e.g. An application is a service (e.g., VPN or web application) that you want to protect. e) that you want to protect with LoginTC.
Create a LoginTC Application in LoginTC Admin Panel, follow Create Application Steps.
If you have already created a LoginTC Application for your deployment, then you may skip this section and proceed to Installation.
Normalize Usernames
Usernames in RD Web are typically in the form “CORP\john.doe”, while in the LoginTC Admin Panel it is generally more convenient to simply use “john.doe”.
Configure Normalize Usernames from the Domain settings by navigating to Domains > Your Domain > Settings.
Select Yes, Normalize Usernames scroll down and click Update.
Follow the instructions to install the LoginTC RD Web Access Connector on a server with the RD Web Access role:
- Download the latest version of the LoginTC RD Web Access Connector
- Run the installer file as a privileged administrator user.
- Press Next.

- Read the License Agreement and press Next if you accept the terms.

- Change the LoginTC API Host only if you have a private enterprise LoginTC deployment. Press Next:

- Enter your LoginTC Application ID and Application API Key. These values are found on your LoginTC Admin Panel. Press Next.

- Choose a secret to use for encrypting and signing RD Web Access sessions. If you already have an RD Web Access secret key, then enter it. Press Next.

- Enable RD Gateway SSO if you plan to install the LoginTC RD Gateway SSO Connector on your RD Gateway server. Press Next.

- Enter your RD Gateway details. See Appendix A: RDP Cert for more information about the signing certificate.

- Choose a RD Gateway SSO Secret Key to use to generate RDG SSO access tokens. Save this key as you will need it for the LoginTC RD Gateway SSO Connector installation. Press Next.

- Press Next.

- Press Finish

The LoginTC RD Web Access Connector is now installed and protecting your RD Web Access. If you selected to use RD Gateway SSO, you should now open the LoginTC RD Gateway SSO Connector Administration Guide and follow the instructions to install the LoginTC RD Gateway SSO Connector.
Installation (RD Gateway SSO)The LoginTC RD Web Access Connector works in conjunction with the LoginTC RD Gateway SSO Connector to protect access to your Microsoft Remote Desktop Gateway with a second-factor LoginTC challenge. To install the LoginTC RD Gateway SSO Connector on a server with the RD Gateway role:
IIS service reset
The installer will restart IIS services upon completion and this will impact other dependent services. We recommend performing these actions during a change windows.
- Download the latest version of the LoginTC RD Gateway SSO Connector
- Run the installer file as a privileged administrator user. The user must have permission to configure and restart IIS.
- Press Next.

- Read the License Agreement and press Next if you accept the terms.

- Enter the SSO Secret that you set when you installed the LoginTC RD Web Access Connector. Press Next.

- Press Install.

- Press Finish.

Direct RD Gateway Access
This RD Gateway will only work with RD Gateway SSO access tokens generated by the LoginTC RD Web Access Connector. If you would like your users to still correct directly to the gateway (instead of going through RD Web Access) then you will need a secondary RD Gateway host.
Network Policy Server
Perform the following steps on the host running the RD Gateway role where you installed the LoginTC RD Gateway SSO Connector.
- Open Network Policy Server from the Start menu on your host running the LoginTC RD Gateway SSO Connector.
- Expand the Policies → Network Policies tree in the side menu.
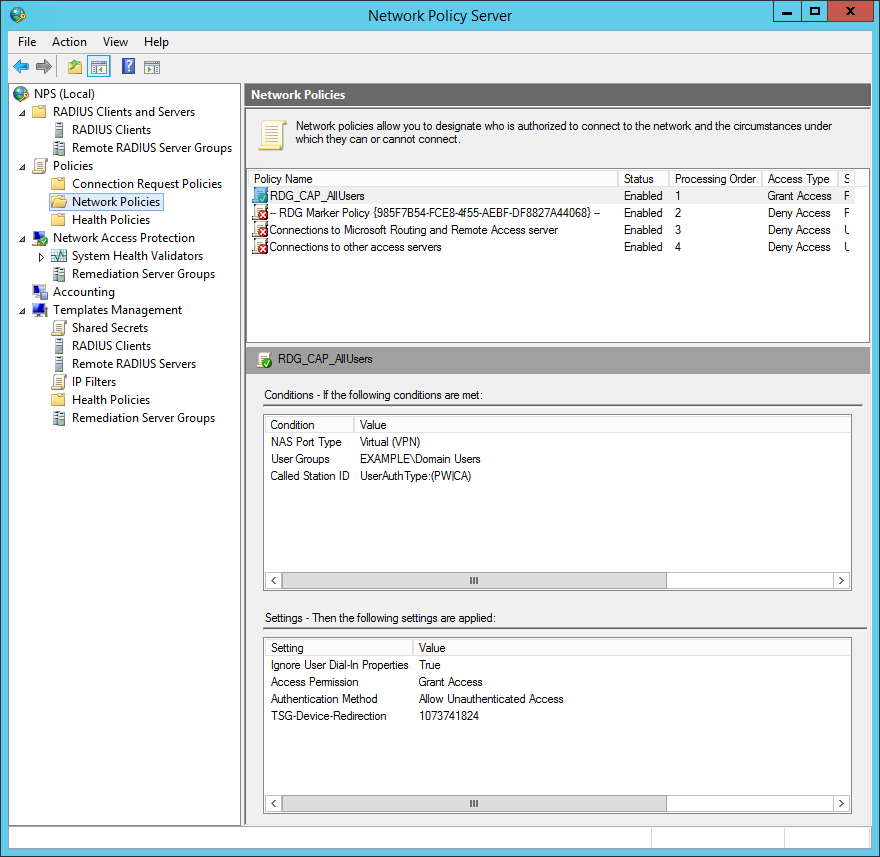
- Right click on the desired target RDG CAP policy (default is RDG_CAP_AllUsers) and click on Properties
- Under the Conditions tab, ensure that
CAis listed in the Called Station ID condition:UserAuthType:(PW|CA).
- Press Apply.
Your users may interact with your RD Web Access deployment in several ways. This chapter details the user experience for each interaction.
User Prerequisites
For the best user experience, the end user should use the following environment to access RD Web Access features:
- Microsoft Windows 7 or higher
- IE8 or higher
Users running Windows with a non-IE browser can launch RDP files using the built-in Remote Desktop Client (supporting RDP 7.0 or higher). Users running OS X can launch RDP files using the Microsoft Remote Desktop Client for Mac.
RD Web Access Usage
When a user navigates to your RD Web Access end-point in their browser they are presented with the standard RD Web Access login page. After successfully logging in with their username and password, they are brought to the LoginTC login page which presents options for the second-factor LoginTC authentication. The user is then brought to the RD Web Access page after successfully authenticating with LoginTC.
The RD Web Access initial login page where the user enters their username and password is unmodified.

After successfully authenticating with their username and password, the user is presented with options to log in with LoginTC. The user may select to authenticate using LoginTC push, bypass codes, or OTPs.

If the user selects LoginTC push, they are informed to approve the LoginTC requst on their device. The user is also presented with an option to remeber their LoginTC login choice. The next time the user logs in they will automatically receive a LoginTC push notification. The user may also cancel the login attempt and return to the login page.

Published Apps Usage
Once logged in, a user launches a published app by clicking on an application icon, which downloads and launches a new dynamically generated RDP file containing an RDG SSO access token. This access token, which is only valid for 60 seconds, is sent to the RD Gateway running the LoginTC RD Gateway SSO Connector to authenticate with the gateway.

RDP File Launching
The RDP file is automatically launched when running Internet Explorer on Windows. All other browsers and operating systems download the RDP file, requiring the user to manually launch the RDP file.
Password Prompt
The RD Gateway SSO access token authenticates the user only to the RD Gateway. The user may still be prompted for their Windows credentials to authenticate with the RD session host if they are not using Windows, or this is their first time connecting, or the user’s computer is not part of the RD session host domain, or the RD session host does not allow remote SSO credential passing. See Enable RDC Client Single Sign-On for Remote Desktop Services.
HTML5 Web Client Usage
After entering their username and password, the user is sent a LoginTC push request. After approving the request, the user is shown their available applications.

The user can then click on an application to launch it.

RD Gateway Considerations
The HTML5 Web Client does not support the LoginTC RD Gateway SSO Connector. To prevent single-factor authentication access directly to the RD Gateway, we recommend limiting RD Gateway access to the internal host running the RD HTML5 Web Client or installing the LoginTC Windows Logon & RDP Connector on the RD Session Host(s).
RemoteApp Usage
The RD RemoteApp web feed allows the user to see a list of the RemoteApp published apps available to them, directly from the Start menu. This is a convenient way for users to launch their remote applications.
The LoginTC RD Web Access Connector protects the Remote Desktop RemoteApp web feed login with an additional LoginTC two-factor challenge. Under normal conditions, a user only authenticates with the RemoteApp web feed once.
RemoteApp user flow:
- The user begins by adding a RemoteApp connections, like normal.

- The user then enters their username and password, like normal.

- The user is presented with a loading spinner while a LoginTC push notification is sent to their device. The user has 60 seconds to approve the request.

- The user is presented with a list of their RemoteApp published apps (which can also be found in the Start menu). Starting a remote app will challenge the user for their Windows credentials and perform authentication with both the RD Gateway and the session host unless the user already has a connection established with the RD session host, in which case, the remote app will open without any additional challenges.

Using RemoteApp and RDG SSO
If you installed the LoginTC RD Web Access Connector with the RDG SSO option then your deployment will require a secondary RD Gateway to support RD RemoteApp. This secondary RD Gateway must not use the LoginTC RD Gateway SSO Connector and must be set as the RD Gateway server in your Remote Desktop deployment configuration. We recommend that you configure this secondary RD Gateway to use the LoginTC RADIUS Connector for authentication so that it’s also protected with two-factor authentication.
The LoginTC RD Web Access Connector logs events to the Microsoft Event Viewer under Applications and Service Logs → LoginTC. LoginTC RD Web Access Connector event logs are helpful in debugging issues.

Passthrough allows you to specify which set of users should be challenged with LoginTC second-factor authentication, and which ones will not. This is often useful when testing and when rolling out a deployment to minimize the impact on others. The passthrough settings are configured on the host running the LoginTC RD Web Access role.
Static User List
Setting a static user list tells the LoginTC RD Web Access Connector which users must be challenged for LoginTC second-factor authentication. All other users will be passed through without requiring a second-factor authentication.
Instructions to set a static list of users to be challenged:
- Navigate to
C:\Program Files\Cyphercor\LoginTC RD Web Access Connectoron the host running the RD Web Access role. - Create a new file
users.txtin Notepad. - Populate the file with a list of users, one line at a time, in the following format:
DOMAIN\username - Save the file.
- Your change will be picked up by the connector within 60 seconds.
If the users.txt file does not exist then all users will be challenged with LoginTC second-factor authentication.
Group List
Setting a group list tells the LoginTC RD Web Access Connector which Active Directory group members must be challenged for LoginTC second-factor authentication. All other users not belonging to any of the listed AD groups will be passed through without requiring a second-factor authentication.
Instructions to set a list of AD groups to be challenged:
- Navigate to
C:\Program Files\Cyphercor\LoginTC RD Web Access Connectoron the host running the RD Web Access role. - Create a new file
groups.txtin Notepad. - Populate the file with a list of AD groups, one line at a time, in the following format:
GROUP NAME - Save the file.
- Your change will be picked up by the connector within 60 seconds.
If the groups.txt file does not exist then all users will be challenged with LoginTC second-factor authentication (unless a static user list file exists).
The LoginTC RD Web Access Connector signs RDP files using your RD Web Access HTTP domain certificate. In order for the signing to work, you must provide the certificate thumbprint during the LoginTC RD Web Access Connector installation, and also grant read access to the IIS process for the certificate.
Follow these instructions to get your certificate thumbprint:
- Run certlm.msc (Manage Computer Certificates) on the host running the RD Web Access role.
- Find your RD Web Access domain certificate (usually under Personal → Certificates).
- Double click on the certificate.
- Press the Details tab.
- Scroll to the bottom of the details and copy the Thumbprint value.

You must grant read access to your RDP signing certificate to the IIS RD Web Access user so the LoginTC RD Web Access module can sign the generated RDP files. To grant permission:
- Run certlm.msc (Manage Computer Certificates) on the host running the RD Web Access role.
- Find your RD Web Access domain certificate (usually under Personal → Certificates).
- Right click on your certificate and click on All Tasks → Manage Private Keys…
- Press the Add button to add a new permission.
- Press the Locations… button and select the local computer.
- Enter
IIS APPPOOL\RDWebAccessinto the textarea and press OK. - Uncheck Full control next to Allow since only Read permissions are necessary.
- Press Apply.

To upgrade the LoginTC RD Web Access Connector / LoginTC RD Gateway SSO Connector, first uninstall the previous version and then install and/or install the newer version.
UninstallationTo uninstall the LoginTC RD Web Access Connector / LoginTC RD Gateway SSO Connector, simply navigate to the Add or remove programs in the Windows Control Panel, find LoginTC RD Web Access Connector / LoginTC RD Gateway SSO Connector in the list and follow the prompts.
Troubleshooting
Email Support
For any additional help please email support@cyphercor.com. Expect a speedy reply.
You may also be interested in our: