Last Updated: March 21, 2025
LoginTC protects access to your WatchGuard Access Portal using SAML SSO. The LoginTC AD FS Connector protects access to your Microsoft Active Directory Federation Services (AD FS) by adding a second factor LoginTC challenge to existing username and password authentication. The LoginTC AD FS Connector provides a LoginTC multi-factor authentication (MFA) method to your AD FS deployment, used by your WatchGuard Access Portal.
Subscription Requirement
Your organization requires the Business or Enterprise plan to use the LoginTC AD FS Connector. Explore Pricing Plans
After clicking on LoginTC from the WatchGuard Access Portal and entering the username and password into the AD FS login page, the user is shown a selection of second factor options. The user clicks a button to receive a LoginTC push notification, authenticates and is logged in.



Authentication Flow
- A user attempts access to WatchGuard Access Portal with username / password
- A SAML request is made to AD FS
- The username / password is verified against an existing first factor directory (i.e. Active Directory)
- The request is trapped by LoginTC AD FS Connector and an authentication request is made to LoginTC Cloud Services
- Secure push notification request sent to the user’s mobile or desktop device
- User response (approval or denial of request) sent to LoginTC Cloud Services
- The LoginTC AD FS Connector validates the user response
- User is granted access to WatchGuard Access Portal
Prefer Reading a PDF?
Download a PDF file with configuration instructions:
Before proceeding, please ensure you have the following:
- WatchGuard appliance with Access Portal support
- WatchGuard Fireware 12.1.1
- LoginTC Admin Panel account
- Active Directory Federation Services (AD FS) Host, Microsoft Windows Server 2016 (or Windows Server 2012)
- WatchGuard Access Portal configured with federation to your on-premise AD FS
WatchGuard Resources:
- Configure the Access Portal
- About SAML Single Sign-On (SSO)
- SAML Requirements for Identity Providers
- Configure SAML Single Sign-On
Working WatchGuard Access Portal Federation Deployment
It is strongly recommended that you have a working WatchGuard Access Portal with federation against your on-premise AD FS prior to adding LoginTC multi-factor authentication.
Create a LoginTC domain in LoginTC Admin Panel. The domain represents a service (e.g. your corporate AD FS) that you want to protect with LoginTC. It will contain token policies and the users that access your service.
If you have already created a LoginTC domain for your AD FS deployment, then you may skip this section and proceed to Installation.
- Log in to LoginTC Admin
- Click Domains:
- Click Create Domain:

- Enter a name and optionally pick an icon

- Scroll down and click Create
Use Default Domain Settings
Domain settings can be modified at any time by navigating to Domains > Your Domain > Settings.
- Download the latest version of the LoginTC AD FS Connector
- Run the installer file as a privileged administrator user on the Windows Server with the AD FS role. Also ensure that the AD FS service is running prior to installing.
- Press Next

- Read the License Agreement and press Next if you accept the terms.

- Change the LoginTC API Host only if you have a private enterprise LoginTC deployment. Press Next:

- Enter your LoginTC Domain ID and Organization API Key. These values are found on your LoginTC Admin Panel. Press Next
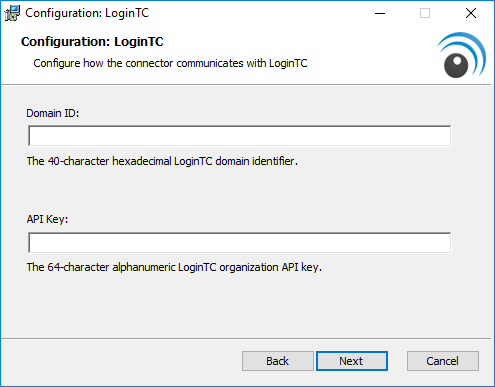
- Press Install. Note that the AD FS service will be restarted during installation and may be temporarily unavailable to your users.

Windows Server 2016 (AD FS version 4.0)
The instructions below are for AD FS (version 4.0) running on Windows Server 2016. If you have AD FS (3.0) running on Windows Server 2012 R2, see AD FS Configuration in Two-factor authentication for AD FS on Windows Server 2012 R2.
To configure your AD FS to use the LoginTC MFA method:
- Open the AD FS Management console.
- Click on the Services > Authentication Policies directory in the left side menu.

- Click on Edit Global Multi-factor Authentication…
- Check LoginTC in the list of MFA methods.

- Press Apply then Ok
- Click on Relying Party Trusts in the left side menu
- Select the Relying Party you wish to add LoginTC MFA to
Don’t have a Relying Party for WatchGuard Access Portal setup yet?
For instructions on configuring a Relying Party for Access Portal see sections WatchGuard Access Portal Configuration and AD FS Relying Party. - Click on Edit Access Control Policy… under Actions in the right sidebar

- Select an access control policy that uses MFA (e.g. Permit everyone and require MFA)
- Press Apply and OK

Your AD FS login will now present the user with a secondary LoginTC authentication page.
Configuration for WatchGuard Access Portal 2FAConfigure WatchGuard Access Portal for SAML Single Sign-On (SSO):
- Log in to your WatchGuard Fireware Web UI:

- Under Subscription Services click Access Portal:

- Click Enable Access Portal:

- Click on the User Connection Settings tab:

- Scroll down and click Configure:
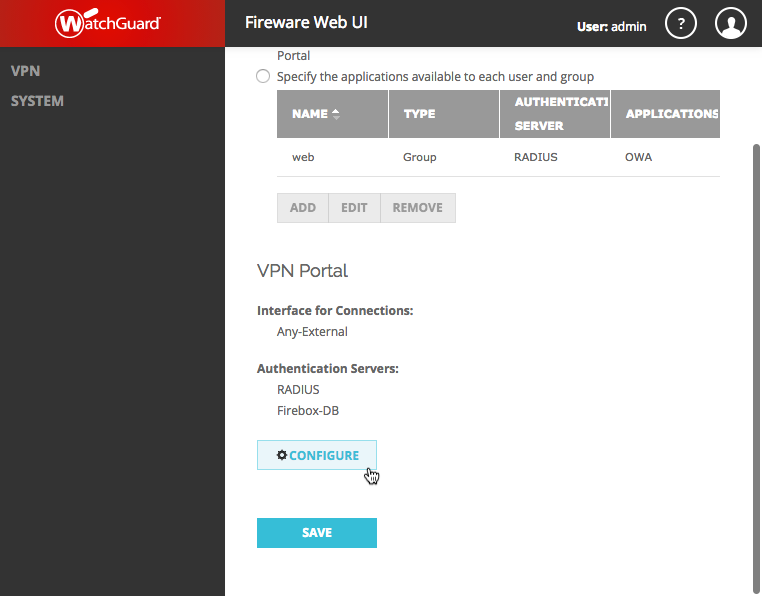
- Click on the SAML tab:

- Click Enable SAML:

- Complete the Service Provider (SP) Settings configuration:

Service Provider (SP) Settings:
| Property | Explanation | Example |
|---|---|---|
IdP Name |
Name to appear as the authentication server name | LoginTC |
Host Name |
A fully qualified domain name that resolves to the Firebox external interface | watchguard.example.com |
- (Continued) Complete the Service Provider (SP) Settings configuration:

Identity Provider (IdP) Settings
| Property | Explanation | Example |
|---|---|---|
IdP Metadata URL |
AD FS Federation Metadata URL | https://fs.example.com/FederationMetadata/2007-06/FederationMetadata.xml |
Group Attribute Name |
The name of the attribute returning group claims | memberOf |
- Click SAVE
- Navigate to SAML 2.0 Configuration for WatchGuard Access Portal page (i.e. https://watchguard.example.com/auth.saml):

- Copy the SP metadata URL found under Option 1 and paste in your browser. Save the file as
metadata.xml.
WatchGuard SAML Configuration
WatchGuard Access Portal is now configured to use your AD FS server to perform authentication. In the next section the metadata.xml file will be used to configure AD FS to properly authenticate WatchGuard Access Portal requests.
To configure a WatchGuard Access Portal Relying Party in AD FS:
- Open the AD FS Management console.
- Click on Relying Party Trusts in the left side menu
- Click on Add Relying Party Trust…
- Select Claims Aware

- Click Start
- Select Import data about the relying party from a file and then browse the where
metadata.xmlfrom the final section of WatchGuard Access Portal Configuration is saved.
- Click Next
- Enter a Display name (for example:
WatchGuard Access Portal):
- Click Next
- Under Choose an access control policy select Permit everyone and require MFA

- Click Next

- Click Close


- Select the Relying Party just created
- Click on Edit Access Control Policy… under Actions in the right sidebar

- Select an access control policy that uses MFA (e.g. Permit everyone and require MFA)
- Press Apply and OK

Next you will need to configured the AD FS Claims for your WatchGuard Access Portal Relying Party.
AD FS ClaimsWatchGuard Access Portal requires the following claims to be configured:
Claim 1: LDAP Attribute for SAM-Account-Name
- Click on Relying Party Trusts in the left side menu

- Select the WatchGuard Access Portal Relying Party
- Click on Edit Claims Issuance Policy… under Actions in the right sidebar

- Click Add Rule
- Select Send LDAP Attributes as Claims and click Next

- Enter a Claim rule name (for example,
Given Name LDAP Query) - Under LDAP Attribute enter SAM-Account-Name
- Under Outgoing Claim Type enter Given Name

- Click Finish
Claim 2: Transform Given Name to Name ID
- Click on Relying Party Trusts in the left side menu

- Select the WatchGuard Access Portal Relying Party
- Click on Edit Claims Issuance Policy… under Actions in the right sidebar

- Click Add Rule
- Select Transform an Incoming Claim and click Next

- Enter a Claim rule name (for example,
Transform Given Name to Name ID) - Under Incoming claim type enter Given Name
- Under Outgoing claim Type enter Name ID
- Select Pass through all claim values
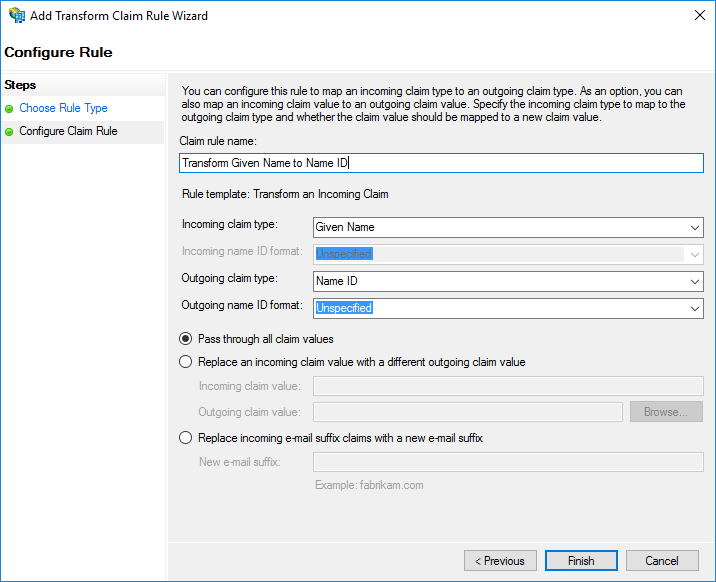
- Click Finish
Claim 3: Group Membership Claim
- Click on Relying Party Trusts in the left side menu

- Select the WatchGuard Access Portal Relying Party
- Click on Edit Claims Issuance Policy… under Actions in the right sidebar

- Click Add Rule
- Select Send Group Membership as a Claim

- Enter a Claim rule name (for example,
Send Group Membership as Claim) - Under User’s group click Browse and select the group configured for WatchGuard Access Portal
- Under Outgoing claim type enter memberOf
- Under Outgoing claim value enter the name of the group. This should match exactly the name configured in the WatchGuard Access Portal

- Click Finish
Additional AD FS Groups
If your WatchGuard Access Portal is configured with multiple groups, subsequent groups can be added as claims following the same procedure listed above
With these claims configured you are now ready to test logging into the WatchGuard Access Portal using LoginTC and AD FS.

The LoginTC AD FS Connector logs events to the Microsoft Event Viewer under Applications and Service Logs → LoginTC. In some cases, it may be helpful to also look at the general AD FS logs under Custom Views → ServerRoles → Active Directory Federation Services.

To uninstall the LoginTC AD FS Connector, simply navigate to the Add or remove programs in the Windows Control Panel, find LoginTC AD FS Connector in the list and follow the prompts.
Prior to Uninstalling
Prior to uninstalling the LoginTC AD FS Connector, ensure that the LoginTC MFA method is not being used in any of your AD FS authentication policies. The uninstallation will fail if the LoginTC MFA method is being used in any of your AD FS authentication policies.
Email Support
For any additional help please email support@cyphercor.com. Expect a speedy reply.